Cyber Security
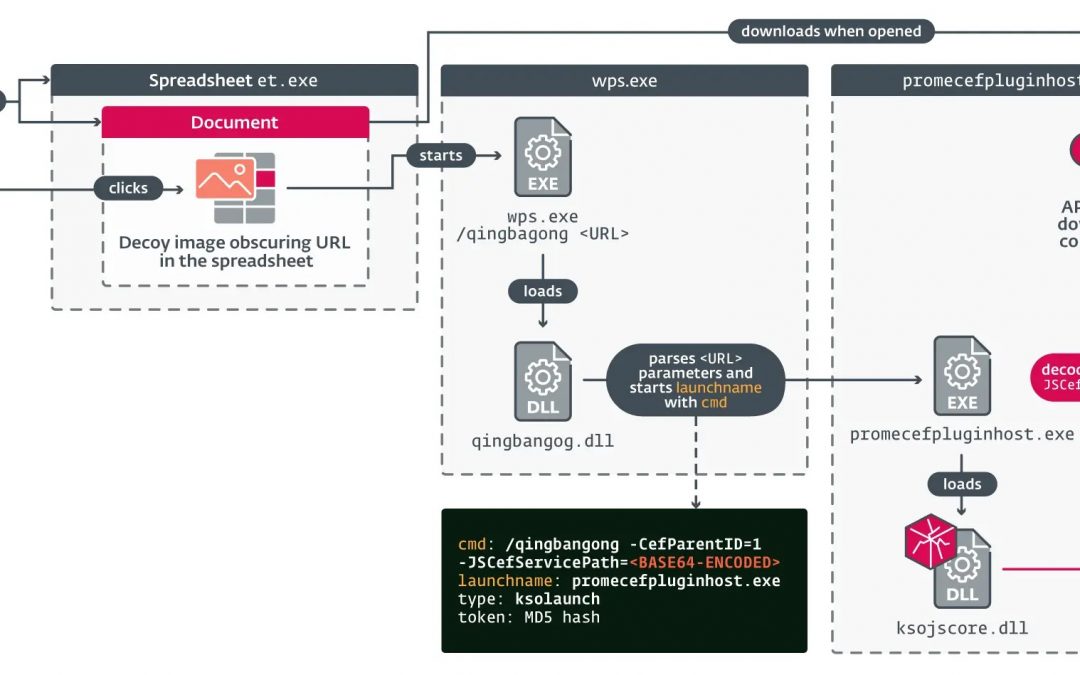
ESET analysts have discovered two crucial previously unknown weaknesses in WPS Office for Windows, which have been utilized by the APT-C-60 advanced persistent threat group. This cyberespionage group aligned with South Korea has been focusing on users in East Asian...
Cyber Security
AI platforms have evolved into indispensable tools for businesses and organizations on a global scale. These advanced technologies offer efficiency and creativity, ranging from chatbots fueled by extensive language models (LLMs) to sophisticated machine learning...
Cyber Security
Safety researchers have found that the BlackByte ransomware group is actively exploiting a just lately patched authentication bypass vulnerability in VMware ESXi hypervisors to deploy ransomware and achieve full administrative entry to sufferer networks. The...

Cyber Security
Hackers focus on legitimate Remote Monitoring and Management (RMM) tools because of their robust and reliable access to systems and networks. This capability enables the extensive and effective distribution of malware throughout an organization’s infrastructure....





