Cyber Security
“`html The realm of cybercrime has undergone a perilous shift as pig butchering schemes now function as all-in-one services, reducing entry hurdles for nefarious individuals globally. The “Penguin” initiative symbolizes an expanding marketplace that...

Cyber Security
“`html Open Source Intelligence (OSINT) has emerged as a fundamental element of cybersecurity threat intelligence. In the contemporary digital domain, organizations encounter an unending stream of cyber dangers, encompassing data breaches, phishing schemes, and...

Cyber Security
“`html A perilous malware risk has emerged targeting Windows users throughout Korea via webhard file-sharing platforms. The Ahnlab Security Intelligence Center has recently uncovered xRAT, also known as QuasarRAT, being disseminated as counterfeit adult games to...

Cyber Security
“`html A shopper makes a purchase. You dispatch. Everyone appears satisfied. Then, a few weeks later, you receive a chargeback. Or you observe the same card being attempted repeatedly in quick succession, failing initially before succeeding. This could signal...

Cyber Security
“`html Cybercriminals are abusing VMware ESXi instances in the wild utilizing a zero-day exploit toolkit that combines several vulnerabilities for VM breaches. The cybersecurity firm Huntress interrupted one such incident, linking the initial breach to an...
Cyber Security
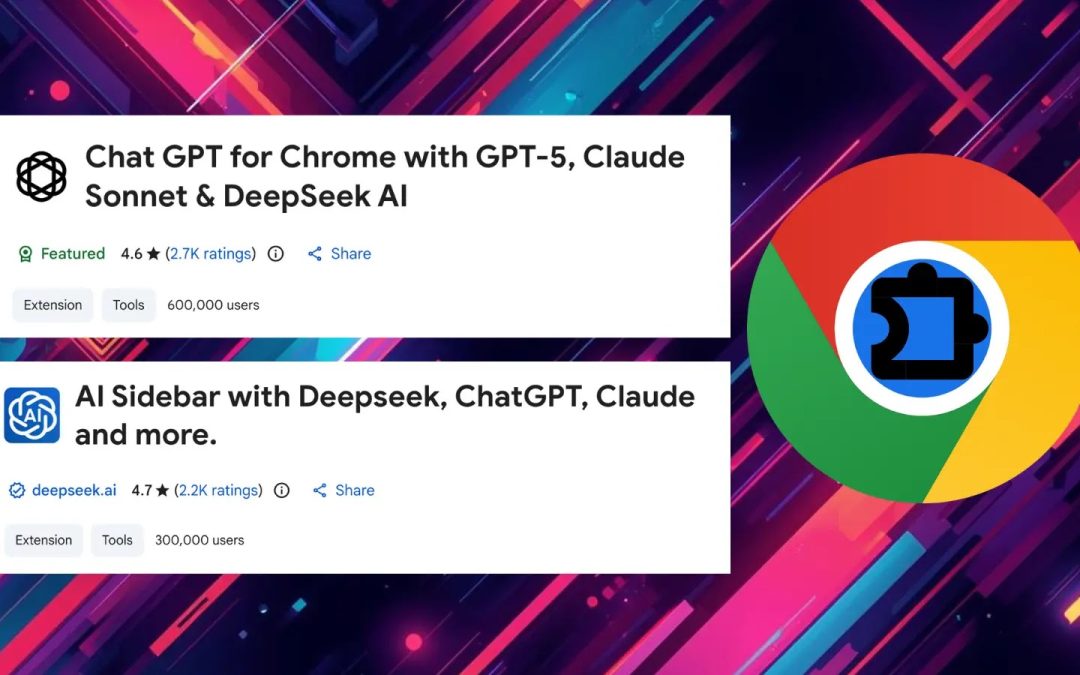
“`html Two malicious Chrome extensions have jeopardized more than 900,000 users by covertly extracting ChatGPT and DeepSeek conversations, along with comprehensive browsing histories, to the attackers’ servers. Uncovered by OX Security analysts, the...







