Essential tools for dynamic analysis of malware are crucial in identifying and comprehending present-day online dangers. These utilities operate suspicious applications in controlled environments to oversee their actions, which entail alterations in files, network communications, or modifications in registries.
Presented below is a compilation of the finest 10 dynamic malware analysis utilities, highlighting their characteristics, advantages, and constraints.
Software such as the cutting-edge ANY.RUN’s Advanced Sandbox equips cybersecurity specialists with robust abilities to identify and scrutinize these enduring methods in real-time. By utilizing the MITRE ATT&CK framework, ANY.RUN streamlines the identification and alleviation of threats.
What Constitutes Dynamic Malware Analysis?
The process of dynamic malware analysis involves the deliberate execution of potentially harmful applications in a controlled setting to observe their immediate actions.
In contrast to static examination, which scrutinizes the code without activating it, dynamic scrutiny engages with the malware to comprehend how it modifies systems and affects networks throughout execution.
This approach proves particularly advantageous in assessing intricate or camouflaged malware that disguises its true intentions via encryption or packaging.
Understanding malware encompasses tracking diverse system engagements to interpret its actions. This encompasses recognizing alterations to the file system by detecting established, altered, or erased files.
The monitoring of networking activities enables the tracing of links to Command-and-Control (C2) servers, specific IP addresses, or domains. Techniques for escaping detection are also recognized, including anti-examination methods like evading sandboxes, detecting virtualization, or encryption practices.
Investigation into system ramifications involves analyzing changes to system elements such as the Windows registry, processes, and services. Additionally, process actions are observed through API invocations, memory insertions, and the creation of subprocesses.
Significance Of Dynamic Malware Analysis
Given the escalating complexity of contemporary malware, dynamic malware scrutiny has emerged as a fundamental component of cybersecurity strategies. Several advantages include:
- Recognition of Advanced Threats:
Dynamic scrutiny can unveil hidden behaviors via obfuscation or encryption, like ransomware payloads, banking trojans, and file-less malware. - Extraction of Indicators of Compromise (IoCs):
Analysts can pinpoint hashes, malicious URLs, IP addresses, and registry entries used in the assault. - Real-Time Observations:
Dynamic analysis offers immediate insights into an attack route, facilitating swifter response and mitigation of incidents. - Contextual Grasp of Attacks:
Security experts can decode the intentions of malware, determining whether it retrieves data, spreads laterally, or installs supplementary payloads. - Boosting Threat Awareness:
Conclusions from dynamic scrutiny contribute to threat awareness by profiling malware families and threat perpetrators.
Operational Mechanics of Dynamic Malware Analysis
Dynamic malware scrutiny encompasses the activation of malware within a controlled, isolated setting to simulate genuine assault scenarios.
Initiating the procedure involves configuring a virtual machine (VM) or sandbox designed to mimic an authentic user environment while ensuring isolation to avert external system breach.
The malware is executed utilizing utilities like ANY.RUN, Cuckoo Sandbox, or Joe Sandbox. Analysts monitor and record its actions, tracking alterations to files, processes, memory, registry, and network communications.
Crucial indicators of compromise (IoCs), such as file hashes, malicious IP addresses, and URLs, are extracted for further scrutiny.
Subsequently, a comprehensive report is produced, summarizing the malware’s actions, IoCs, and potential repercussions, which can be disseminated to incident response teams or incorporated into security systems.
Techniques Deployed in Dynamic Malware Analysis
Dynamic malware analysis integrates an amalgamation of utilities and strategies to unveil malware activities:
The information is presented in a structured table format below:
| Analysis Genre | Explanation | Example |
|---|---|---|
| Behavioral Analysis | Surveys system modifications, network interactions, and memory utilization. | Scrutinizing a trojan that links to a distant server for data extrusion. |
| API Call Monitoring | Traces API calls initiated by malware to comprehend system-level interactions. | Monitoring calls to APIs like RegCreateKey or CreateFileW. |
| Network Traffic Examination | Enumerates malevolent activities such as DNS queries, HTTP solicitations, or data extrication. | Harnessing tools like Wireshark to analyze traffic to a Command-and-Control server. |
| Memory Scrutiny | Delves into malware that functions exclusively within system memory (file-less malware). | Utilizing tools like Volatility to extract and analyze memory dumps. |
| User Interaction Imitation | Some malware triggers solely post specific user engagements, like activating macros or clicking on pop-ups. | Interactive tools like ANY.RUN enable analysts to emulate these interactions. |
Top Selection from Cyber Security News
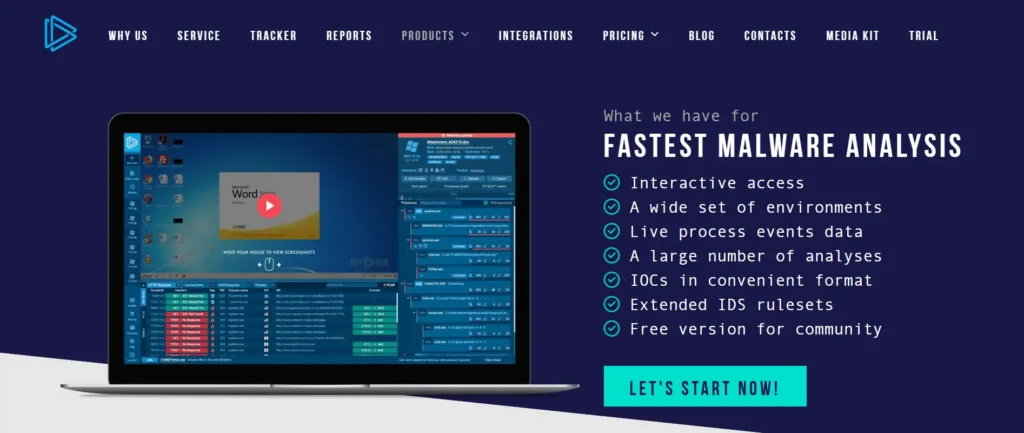
Securing the leading position is ANY.RUN, an immensely interactive, cloud-based sandbox that stands out for its hands-on, instantaneous approach to evaluating malicious samples. Let’s delve deeper into the tools.
ANY.RUN serves as an innovative, cloud-facilitated malware analysis facility that empowers users to interact with malware samples instantaneously.
In contrast to conventional sandboxes that operate automatically, ANY.RUN furnishes analysts with the flexibility to manually interact with files, a feature particularly beneficial when scrutinizing malware necessitating user intervention to activate payloads.
Principal Traits of ANY.RUN:
- Instant Interaction:
Operators can stimulate malware manually by replicating clicks, keystrokes, or alternative actions. This capability proves invaluable in evaluating sophisticated malware such as ransomware or droppers reliant on user interactions for executing their assault sequence. - Dynamic Visualization:
ANY.RUN offers an intricate and user-friendly process tree, showcasing eventssuch as working with files, making changes to the registry, and engaging in network operations in real-time. - Thorough Network Monitoring:
This utility captures and presents all network activity, encompassing DNS requests, HTTP queries, and C2 exchanges. It allows for the download of PCAP files for more in-depth scrutiny with tools like Wireshark. - Identification of Indicators of Compromise (IoCs):
Automatically compiles a roster of IoCs, including IP addresses, domains, hash values of dropped files, and malevolent URLs. - Interactive Work Atmosphere:
Operators can collaborate in real-time, rendering it an exceptional resource for response teams dealing with incidents. - Extensive File Format Support:
Encompasses a broad spectrum of malicious file types, comprising executables, scripts, documents, and URLs.
Top 10 Effective Tools for Dynamic Analysis of Malware
| Top 10 Dynamic Analysis Tools for Malware | Characteristics | Stand-alone Functionality | Pricing | Availability of Free Trial / Demo |
|---|---|---|---|---|
| 1. ANY.RUN | Live interaction, dynamic visualizations, cooperation, analysis of network traffic, and adaptability of environments. | Interactive, real-time analysis tool for malware | Offers a free tier; paid packages commence from $109/month. | Accessible |
| 2. Cuckoo Sandbox | Source code available, tracking of API calls, monitoring of network traffic, provision of virtualized environments, support for diverse file formats. | Open-source solution for automated examination of malware | Open-source solution; no charge for usage. | Available |
| 3. Joe Sandbox | Compatibility across platforms, detailed memory forensic analysis, integration with YARA rules, extraction of IoCs. | Advanced multiform malware analytical platform | Commences at $4,999/year for Pro cloud editions. | Available |
| 4. Hybrid Analysis | Cloud-oriented, generation of IoCs automatically, amalgamation of static and dynamic analyses, assignment of severity scores. | Cloud-centric intelligence and sandbox for malware | Utilization is free of charge. | Available |
| 5. FireEye Malware Analysis | High-grade solution for enterprises, zero-day detection capabilities, connection with threat intelligence, memory forensics examination. | Enterprise-grade detection and examination of malware | Pricing details not publicly disclosed; inquire for a quote. | Available |
| 6. Detux (Linux-Focused) | Open-source nature, focus on Linux-based malware analysis, modular construction, monitoring in real-time. | Linux-centered sandbox for malware analysis | Open-source project; no cost involved. | Available |
| 7. Cape Sandbox | Separating payloads, backing for packed malware, provision of detailed reports, enhancement of Cuckoo Sandbox functionalities. | Sandbox rooted in Cuckoo architecture with process injection | Open-source software; no charge for usage. | Available |
| 8. MalwareBazaar Sandbox | Cloud-centric sandbox free of charge, elaborated reports on malicious behavior, emphasis on IoC generation. | Platform for sharing and analyzing malware samples | Cost-free service. | Available |
| 9. Remnux | Toolkit based on Linux, examination of network traffic, capabilities for reverse engineering, wide array of tool integrations. | Software toolkit for reverse engineering malware based on Linux | No charges for utilization. | Available |
| 10. Intezer Analyze | Detection of code reuse using binary DNA technology, swift analysis, classification of complex malware families. | Analysis for categorization of malware based on code reuse | Offers a free tier; contact for premium pricing. | Available |
1. ANY.RUN (Most Comprehensive)
ANY.RUN represents a highly interactive sandbox hosted in the cloud, explicitly crafted for real-time examination of malware. Diverging from conventional sandbox environments, it empowers analysts to manually engage with harmful files to imitate user operations (e.g., clicking, typing), thereby unmasking concealed behaviors.
This attribute renders ANY.RUN exceedingly suitable for scrutinizing ransomware, delivery mechanisms, and malware reliant on user inputs for full functionality. Furthermore, it champions collaborative workflows, making it an exceptional selection for Security Operations Centers (SOCs).
Equipped with live collaboration capabilities, multiple analysts can jointly operate on the same session, ensuring prompt incident responses.
The rich arsenal of tools it features, inclusive of TI Lookup, YARA Search, and Feeds, empowers users to delve into threats, monitor malevolent engagements, and collaborate with maximum efficiency.
Through ANY.RUN, security teams can:
- Detect malware swiftly
- Engage with samples in real-time
- Economize time and resources by eliminating the need for sandbox configuration and upkeep
- Document and scrutinize every facet of malware behavior
- Scale their operations as required
Salient Features:
- Interactive Real-Time Engagement: Analysts can trigger malware activities by simulating user actions.
- Dynamically Visualized Data: Offers real-time detailed displays of process hierarchies, file alterations, and network connections.
- Extraction of IoCs: Automatically compiles lists of indicators of compromise (IoCs) like file hashes, malevolent IPs, and domains.
- Enhanced Collaboration: Permits multiple analysts to collaborate on a single analysis session.
- Customization of the Environment:Environments: Analysts have the capability to set up virtual machines (e.g., Windows 10) with specific configurations to replicate actual scenarios.
| What’s Great? | Room for Improvement? |
|---|---|
| User-friendly interface for beginners. | Organizations with strict policies may not find it suitable due to cloud dependency. |
| Perfect for analyzing malware that requires user interaction. | Advanced features are restricted to paid versions only. |
| Outstanding collaborative tools for team analysis. | |
| Real-time execution with detailed visual representations. |
2. Cuckoo Sandbox
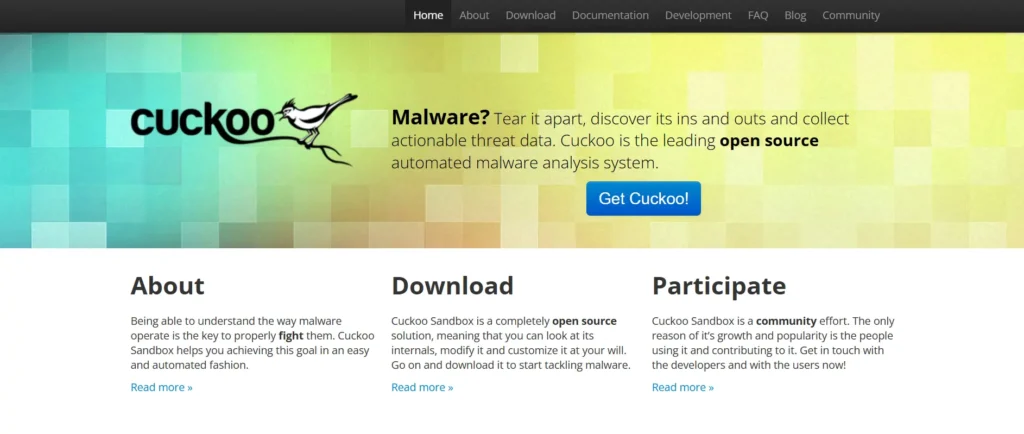
Overview:
Cuckoo Sandbox stands out as a well-known open-source tool for analyzing malware. It offers a versatile and scalable environment for running and monitoring malicious files in various formats, such as documents, scripts, and executables.
Its modular structure allows extensive customization, empowering analysts to enhance its capabilities through plugins or integrate with tools like YARA rules, Suricata for detecting intrusions, or Volatility for memory forensics.
Notable Features:
- Tracks API calls, file modifications, and network activities.
- Compatible with virtualized, physical, or cloud setups.
- Generates comprehensive JSON or HTML reports for further scrutiny.
| What Stands Out? | Areas for Enhancement? |
|---|---|
| Free to utilize and highly adaptable. | Requires technical proficiency for installation and upkeep. |
| Compatible with various file types and operating systems. | New users might find the initial setup time-consuming. |
| Seamless integration with tools like YARA and Suricata. |
3. Joe Sandbox
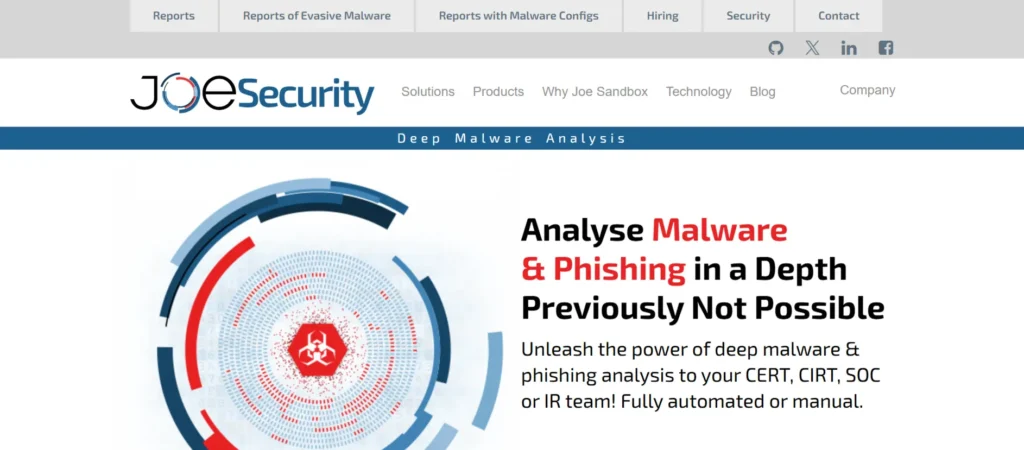
Overview:
Joe Sandbox is a commercial solution known for its extensive analysis capabilities across multiple platforms, including Windows, Linux, macOS, Android, and iOS.
It covers a wide range of file formats and goes beyond basic dynamic analysis by simulating user interactions to reveal hidden malicious behaviors.
With its profound memory forensics capabilities, Joe Sandbox excels in investigating complex threats like APTs or state-sponsored attacks.
Key Features:
- Supports multiple platforms for cross-OS threat analysis.
- Detailed memory analysis and process emulation.
- Integration of YARA rules for customized threat detection.
| Highlights | Opportunities for Improvement |
|---|---|
| Cross-platform support for OS-spanning analysis. | High licensing costs restrict accessibility for smaller entities. |
| Great for deciphering advanced threats. | Beginners might feel overwhelmed by its feature set. |
| Advanced memory forensics and process emulation. |
4. Hybrid Analysis (CrowdStrike Falcon Sandbox)

Overview:
Hybrid Analysis, now part of CrowdStrike, emerges as a well-liked cloud-based sandbox tool that automates malware analysis by blending static and dynamic methods.
It includes a crowd-sourced database for malware intelligence, enabling analysts to compare results and gain insights into ongoing malicious campaigns.
Its automated classification system assigns severity scores to samples, making it a top choice for swift evaluation of malicious files.
Key Features:
- Integration of behavioral and signature-based analysis.
- Severity scoring for samples based on suspicious behaviors.
- Cloud-based with minimal setup requirements.
| Strengths | Room for Enhancement |
|---|---|
| Basic usage available with a free tier. | Customization options are limited when compared to other tools. |
| Efficient for prompt threat evaluation. | Relies on external tools for advanced configurations. |
| Enriched analysis through a crowd-sourced threat database. |
5. FireEye Malware Analysis
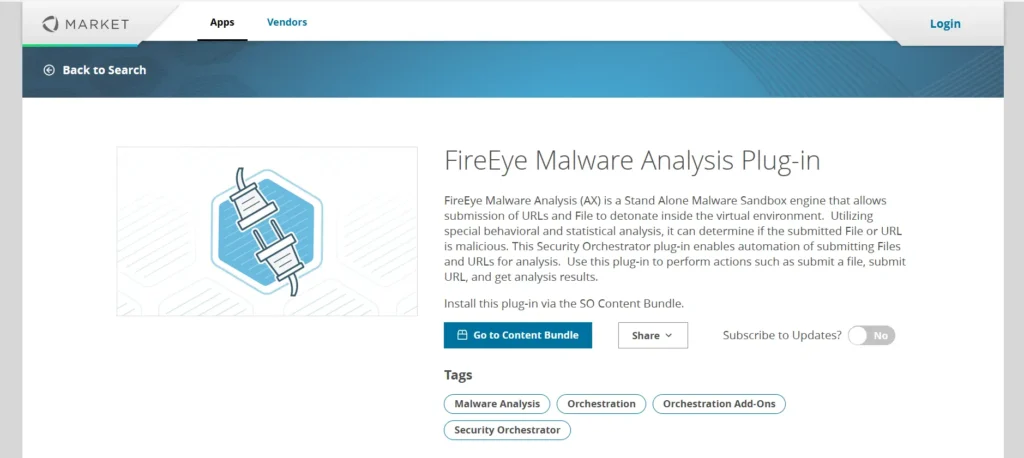
Overview:
FireEye’s malware analysis platform is tailored for corporate environments, offering sophisticated tools to detect zero-day threats, fileless malware, and advanced persistent threats (APTs).
By integrating with the FireEye Threat Intelligence network, organizations gain attribution data for attacks, identify threat actors, and track attack campaigns.
Being ideal for large entities focused on cyber resilience, it is a preferred choice.
Key Features:
- Behavioral and memory analysis of malware.
- Integration with FireEye Threat Intelligence for attack tracking.attribution
- Assists in thorough fileless malicious software examination.
| Advantages | Areas for Improvement |
|---|---|
| Specially designed for large enterprises with advanced requirements. | Pricy, hence not accessible for smaller enterprises. |
| Outstanding at identifying fileless and memory-resident malware. | |
| Seamless integration with FireEye’s threat intelligence. |
6. Detux (Linux-Focused)
Summary:
Detux is a sandbox open-source tool specifically tailored for the analysis of Linux-based malware, making it invaluable for organizations focused on cloud, IoT, or server security.
As Linux is increasingly targeted by cybercriminals, Detux offers a crucial solution for analyzing cryptojackers, rootkits, and other Linux-focused threats in real time.
Notable Features:
- Records file, network, and system-level activities.
- Facilitates Linux ELF binary analysis.
- Modular design for extensibility.
| Advantages | Areas for Improvement |
|---|---|
| Specifically crafted for Linux ELF binaries. | Restricted to Linux malware analysis—no cross-platform support. |
| Efficient and easy to integrate into workflows. | Requires expertise to set up and customize effectively. |
| Free and open-source. |
7. Cape Sandbox
Summary:
Built on Cuckoo Sandbox, Cape specializes in capturing, unpacking, and analyzing obfuscated or packed malware, making it a core tool for researchers who need to analyze advanced malware like Emotet or TrickBot.
By focusing on payload extraction and de-obfuscation, Cape helps analysts identify the true intent of packed or encrypted malware.
Notable Features:
- Payload extraction and decryption.
- Detection of fileless malware.
| Advantages | Areas for Improvement |
|---|---|
| Exceptional for unpacking heavily obfuscated malware. | Less intuitive than GUI-based solutions like ANY.RUN. |
| Supports fileless malware and complex attack chains. | Requires a learning curve for new users. |
| Enables integration with Cuckoo plugins. |
8. MalwareBazaar Sandbox
Summary:
Part of Abuse.ch’s ecosystem, MalwareBazaar Sandbox is a free cloud-based tool designed for analyzing malware submitted to the public MalwareBazaar platform.
It is particularly useful for tracking and understanding the evolution of malware families, making it a favorite among threat researchers who want to keep up with the latest trends in malicious campaigns.
Notable Features:
- IoC generation for new malware samples.
- Scalable cloud-based architecture.
| Advantages | Areas for Improvement |
|---|---|
| Free and user-friendly for researchers. | Limited to analyzing public malware samples. |
| Excellent for tracking malware campaigns. | Less advanced than paid alternatives for in-depth analysis. |
| Scalable cloud infrastructure. |
9. Remnux
Summary:
Remnux is a Linux-based toolkit preloaded with a wide range of tools for analyzing and reverse engineering malicious software.
It is highly efficient for analyzing network-focused threats, such as botnets and DDoS malware, and includes pre-installed tools like Wireshark for packet analysis, Radare2 for debugging, and Binwalk for firmware analysis.
Notable Features:
- Pre-installed tools for debugging, reverse engineering, and network forensics.
- Lightweight Linux distribution.
| Advantages | Areas for Improvement |
|---|---|
| Free and user-friendly for researchers. | Limited to analyzing public malware samples. |
| Excellent for tracking malware campaigns. | Less advanced than paid alternatives for in-depth analysis. |
| Scalable cloud infrastructure. |
10. Intezer Analyze
Summary:
Intezer Analyze focuses on code reuse analysis, mapping new malware samples to known families using binary DNA technology. By identifying similarities in reused code, it provides actionable insights into the malware’s ancestry and potential links to known threat groups.
This approach makes it particularly valuable for uncovering connections between new threats and existing attack campaigns.
Notable Features:
- Identifies code similarities across malware families.
- Binary DNA technology for malware classification.
| Advantages | Areas for Improvement |
|---|---|
| Maps malware to known families using unique DNA technology. | Limited capabilities for real-time behavioral analysis. |
| Great for connecting new malware to existing campaigns. | |
| Fast and efficient for polymorphic malware. |
Conclusion
Dynamic tools for analyzing malware are crucial for cybersecurity professionals aiming to identify and counter advanced threats. Among the top tools, ANY.RUN excels in its interactivity and real-time capabilities, making it an exceptional choice for SOCs and independent researchers alike. Whether you require an open-source solution like Cuckoo Sandbox or a specialized tool like Detux for threats specific to Linux, there is an option here to suit your requirements. Select the appropriate tool for your organization and enhance your malware analysis capabilities.
The post Top 10 Best Dynamic Malware Analysis Tools in 2025 appeared first on Cyber Security News.