“`html
An advanced cyber initiative is taking advantage of the confidence users have in well-known collaborative software, deceiving them into installing a compromised version of Microsoft Teams to secure remote access to their systems.
Malicious actors are employing search engine optimization (SEO) manipulation and nefarious advertisements to attract unaware victims to counterfeit download sites, a strategy that closely resembles past campaigns utilizing other trustworthy software.
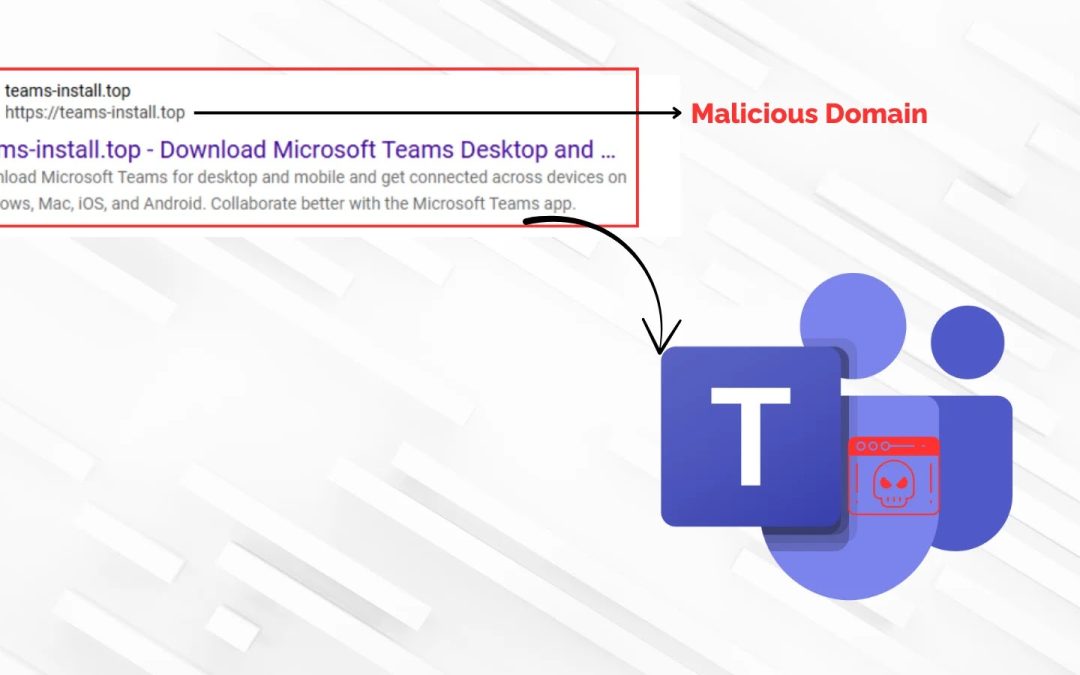
Blackpoint has detected a fresh wave of assaults where individuals searching for “Microsoft Teams download” are confronted with harmful ads that lead them to fake websites.
One such site, teams-install[.]top, has been noted to mimic the official Microsoft download page, providing a harmful file labeled MSTeamsSetup.exe.
To appear authentic, these fraudulent installers are often endorsed with dubious digital certificates from entities like “4th State Oy” and “NRM NETWORK RISK MANAGEMENT INC.”. This method aids in evading simple security measures that identify unsigned applications.

Weaponized Microsoft Teams Delivers Oyster Backdoor
Launching the counterfeit installer initiates a multi-layered assault that deploys a persistent backdoor known as Oyster, or Broomstick.
The malware installs a harmful DLL file named CaptureService.dll into the %APPDATA%Roaming directory and ensures persistence by creating a scheduled task titled CaptureService.
This task is arranged to execute the DLL at regular intervals, guaranteeing the backdoor stays operative even post system reboot and allowing it to merge with typical Windows processes.
The Oyster backdoor grants attackers a substantial foothold within the compromised network.
It facilitates remote access, gathers system data, and establishes communication with command-and-control (C2) servers to exfiltrate information and receive further directives or payloads.
In this initiative, Oyster has been noted communicating with C2 domains such as nickbush24[.]com and techwisenetwork[.]com, as revealed by Blackpoint analysis unveiled.

This initiative is not an isolated event but part of a larger pattern where cybercriminals weaponize recognizable software brands to obtain initial access. The methods are akin to previous operations that disseminated fake installers for PuTTY, WinSCP, and Google Chrome.
By capitalizing on malvertising and SEO manipulation, attackers can effectively target a broad audience, exploiting user confidence in both search engines and popular enterprise solutions.
The incorporation of the Oyster backdoor raises significant concerns, as it has been associated with ransomware operations like Rhysida, which have utilized it to penetrate corporate networks.
This approach underscores a transition where threat actors are not merely depending on phishing emails but are actively contaminating the software supply chain at the user-download stage.
The initiative is tailored to evade several conventional antivirus and endpoint detection and response (EDR) solutions, rendering it a stealthy and perilous threat.
To reduce this risk, organizations and individuals are highly recommended to obtain software solely from authorized vendor websites.
Utilizing saved bookmarks for frequently visited download sites is preferable to relying on search engine outcomes, particularly sponsored advertisements. Awareness and user education remain essential defenses against these advancing social engineering techniques.
“`