An elaborate malware initiative aimed at Latin American users has surfaced as a notable peril to the region’s financial industry, with cybercriminals utilizing the DCRat banking trojan through intricate phishing strategies intended to expropriate financial credentials.
These malicious activities, which have escalated throughout 2024 and into 2025, signify an increasing worry for cybersecurity specialists throughout Colombia and adjacent nations as threat actors capitalize on trusted institutional communications to distribute their malicious payloads.
DCRat, a Malware-as-a-Service model that has circulated since at least 2018, has obtained substantial traction in underground cybercrime forums where it is marketed for around seven dollars for a two-month subscription.
The malware’s availability and extensive feature set have rendered it an appealing choice for financially driven threat actors aiming to gain ongoing access to victim systems and extract sensitive banking details from unsuspecting individuals throughout the region.
IBM analysts recently recognized that the threat group Hive0131, thought to originate from South America, has been orchestrating these campaigns with a specific emphasis on Colombian users through highly convincing email impersonation strategies.
The group has exhibited notable sophistication in their social engineering tactics, crafting messages that seem to stem from authentic Colombian judicial institutions, particularly imitating correspondence from The Judiciary of Colombia and the Civil Circuit of Bogota to create compelling lures for prospective victims.
The ongoing campaign signifies a significant progression in the threat landscape, as attackers have honed their delivery methods to encompass multiple infection vectors that circumvent traditional security measures.
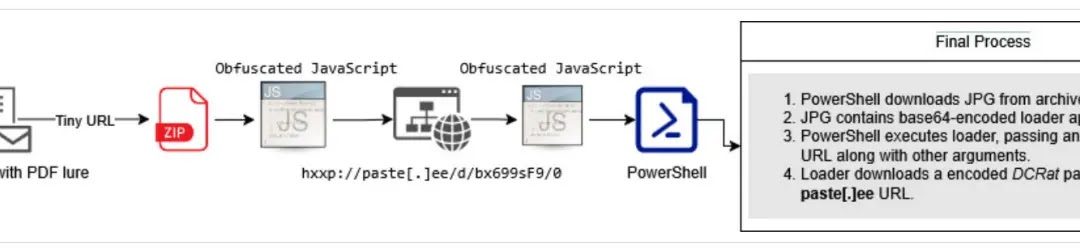
Unlike prior campaigns noted in 2024 that relied heavily on password-protected RAR archives containing NSIS installers, the current operations employ a more intricate technique involving obfuscated JavaScript files and specialized loaders aimed at evading detection by security software and analysis environments.
Advanced Infection Mechanisms and Detection Evasion
The technical prowess of these attacks is centered around a custom malware loader termed VMDetectLoader, which acts as the main delivery mechanism for the DCRat payload.
IBM researchers uncovered that this loader, recognized by the hash 0df13fd42fb4a4374981474ea87895a3830eddcc7f3bd494e76acd604c4004f7, is based on an open-source project specifically crafted for virtual machine detection and evasion.
The loader employs numerous sophisticated methods to assess whether it is functioning within a sandbox or analysis environment before continuing with payload deployment.
.webp)
VMDetectLoader showcases remarkable technical intricacy through its multi-stage execution process, initiating with environment fingerprinting and moving through meticulous payload retrieval and injection.
The malware examines system details including motherboard information, searching for signs of virtualization technologies such as VMware, QEMU, VirtualBox, and Microsoft Hyper-V before deciding whether to continue with the infection chain.
When the loader determines it is functioning in a secure environment, it initiates a process hollowing injection method, generating a suspended MSBuild.exe process and substituting its memory contents with the DCRat payload using a series of Windows API calls including CreateProcess(), ZwUnmapViewOfSection(), VirtualAllocEx(), and WriteProcessMemory().
The post DCRat Attacking Users In Latin America To Steal Banking Credentials appeared first on Cyber Security News.