The actors behind Akira Ransomware are working on a Rust Variant to target ESXi servers. Initially detected in March 2023, this ransomware is designed to infiltrate both Windows and Linux systems.
Utilizing a double-extortion strategy, this ransomware strain has impacted numerous organizations, especially in the U.S. Cisco Talos cybersecurity analysts recently uncovered the active development of a rust variant by the Akira ransomware group to target ESXi servers.
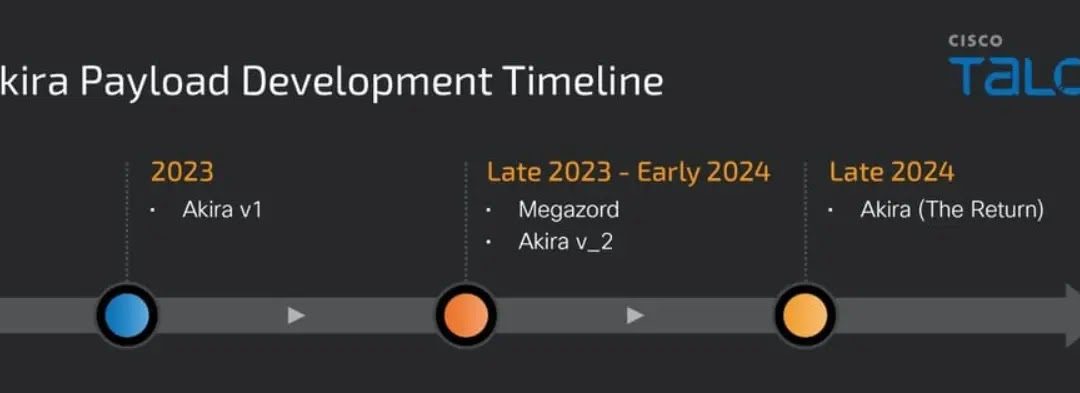
Akira ransomware has emerged as a formidable cybersecurity threat, continuously refining its attack methods in a sophisticated manner throughout 2024.
Akira Ransomware New Rust Variant
The technical architecture of this ransomware underwent a significant “transformation,” moving from “C++” to the “Rust” programming language.
This transformation mainly occurred in its “ESXi encryptor variant” (‘version 2024.1.30’), now employing the “rust-crypto 0.3.26 library” instead of the previous “Crypto++ library.”
Akira’s operators exploit critical vulnerabilities such as “CVE-2024-40766 in SonicWall SonicOS,” “CVE-2023-20269 in Cisco VPN services,” and “CVE-2023-48788 in FortiClientEMS software” for unauthorized access.
Upon penetrating a network, they utilize advanced methodologies like “PowerShell scripts” for credential harvesting, “WMI” for erasing system shadow copies (“Get-WmiObject Win32_Shadowcopy | Remove-WmiObject”), and “RDP” for lateral movement.
The ransomware has diversified its targets to encompass both “Windows” and “Linux” environments, with its latest variant appending the distinct “akiranew” extension to encrypted files and deploying the Megazord encryptor alongside its main payload.
Their attack sequence kicks off with “compromising VPN credentials” and “exploiting network appliances,” leading to “privilege escalation” through tools like “Veeam.Backup.
MountService.exe.” Predominantly, the manufacturing and professional technical services sectors are the primary targets.
They achieve persistence through intricate evasion tactics like “binary padding” and “security tool manipulation.”
Moreover, it appears that the Akira ransomware group is strategically reverting from their “Rust-based Akira v2 variant.” They are reverting to their traditional “C++ programming approach” for both “Windows” and “Linux” encryption tools.
This strategic shift places operational robustness above innovation, as evidenced by their “September 2024 samples,” which retained the familiar extension and notes:-
- .akira file extension
- akira_readme.txt ransom notes
The report indicates that by reducing quarter-round operations, the group has technically elevated its strategy by implementing the “ChaCha8” stream cipher, offering more efficient encryption operations than the previously utilized “ChaCha20” algorithm.
The Windows variant now includes new parameters like “-localonly” and “–exclude,” avoiding encrypting system paths such as “$Recycle.Bin” and “System Volume Information.”
The Linux version maintains the “–fork” parameter for generating child processes during encryption and aims at specific file extensions like:
- .4d
- .abd
- .abx
- .ade
- .ckp
- .db
- .dddpl
- .dx
- .edb
- .fo
- .ib
- .idb
- .mdn
- .mud
- .nv
- .pdb
- .sq
- .te
- .ud
- .vdh
In streamlining their operations, the group has gradually reduced its toolset, with the latest being “Megazord” utilized for Windows environments. Their primary focus remains on targeting “VMWare’s ESXi” and “Linux environments.”
These platforms enable the simultaneous encryption of multiple VMs and crucial workloads through “vmdk” files, maximizing operational impact while minimizing the necessity for extensive lateral movement and credential theft within targeted networks.
Recommendations
Below, we outline all the recommendations:-
- Regularly evaluate vulnerabilities and implement security patches on ESXi hosts.
- Enforce robust password guidelines and activate MFA.
- Implement “SIEM” and “EDR/XDR” for continuous monitoring and response to threats.
- Strengthen ESXi interfaces with access controls, MFA, and RBAC.
- Turn off unnecessary WMI access and monitor WMI commands.
- Guard against credential dumping with Windows Defender Credential Guard.
The post Akira Ransomware Actors Developing Rust Variant To Attack ESXi Servers appeared first on Cyber Security News.