The circumstances revolving around the apprehension of Pavel Durov on 24 August 2024 for suspected operational infractions by Telegram exacerbated discussions regarding digital confidentiality, peer-to-peer encryption, and the accountability of online platforms.
This instance also depicts the confrontation between law enforcement and secure messaging applications.
Pavel Durov is considered in hacktivist communities as the originator of both Vkontakte (VK) and Telegram, so why is there such a dispute concerning the MTProto encryption protocol and Telegram’s cloud storage framework?
In the past, VK was substantial chiefly due to the facilitation of the API and absence of content moderation, which unintentionally facilitated the establishment of a network.
It has provoked inquiries about the safety of communication apps due to potential backdoors and resurrected the discourse regarding national security versus user privacy in the contemporary world.
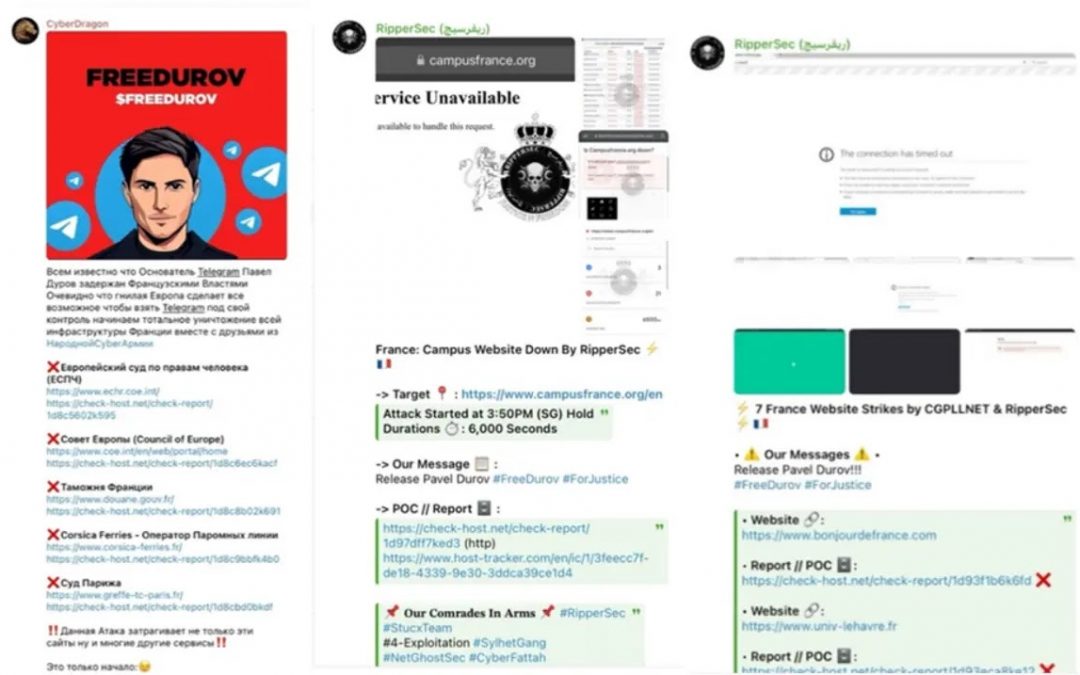
The #FreeDurov – Hacktivists Rally
Due to its minimal censorship and Durov’s libertarian stances, Telegram swiftly evolved into a hub for pro-Russian hacktivist factions such as UserSec, People’s Cyber Army, and CyberDragon groups.
Provided below are the names of major Russian hacktivist groups and their associates:
- People’s Cyber Army
- UserSec
- CyberDragon
- EvilWeb
- Rootsploit
- CGPlnet
- Overflame
- ReconSploit
- RipperSec
- 62IX (played a supporting role in the #freedurov initiative)
- High Society (coalition)
- Holy League (coalition)
The arrest of Durov in France on 24 August 2024 spawned the #FreeDurov and #OpDurov movements, bringing together previously opposing segments of Russian society.
This scenario also led to a series of Denial of Service (DOS) assaults and allegations of breaches against French and EU computing networks and systems.
It is essential to acknowledge that UserSec has been implicated in assaults against the French Court of Cassation and the Administrative Court of Paris, while the People’s Cyber Army breached Industrial Control Systems (ICS) at the Parc Eolien de Tenbonrev wind farm, located in Brittany, and managed the electricity distribution control consoles.
The coordinated attack extended beyond merely compromising actions by terrorist entities and links to critical infrastructure but also encompassed their synchronized strikes against airports, ferry services, the financial systems of the AXA Group, or educational establishments like the Agence Universitaire de la Francophonie (AUF), showcasing the hacktivists’ capability for multifaceted assaults on vital infrastructure.
.webp)
The leak in mid-August 2024 of the “Kordon 2023” FSB Border Service database on Telegram channels revealed Pavel Durov’s 50+ trips to Russia during 2014-2023, contradicting his purported disconnection from the nation.
A revelation containing the aforementioned details emerged just before Durov’s detention in Paris, with it being noteworthy that during one such visit, Roskomnadzor lifted the prohibition on Telegram.
This incident catalyzed the emergence of the #FreeDurov campaign, enlisting Telegram-based pro-Russian, pro-Palestinian, and French hacktivists.
This occurrence delineates the tension between the regulatory mandates of national authorities concerning content moderation and the entitlement to privacy of users within the realm of social networking services. It might cast ramifications on digital correspondence and the safeguarding of users’ communication in the times ahead.
The post #FreeDurov – Hacktivists Rally On Telegram For CEO Pavel’s Release appeared first on Cyber Security News.