Business Email Compromise (BEC) incidents don’t require malware to inflict harm. Just one persuasive message; a counterfeit login request, a skillfully camouflaged link, and an employee’s credentials vanish.
From this point, cybercriminals can discreetly infiltrate inboxes, extract confidential documents, and impersonate executive personnel for monetary deceit.
The most concerning aspect is that these incidents often evade standard email filters and antivirus applications.
That’s the reason security teams are adopting solutions like interactive sandboxing to identify what automated methods may overlook.
What Makes BEC So Challenging To Identify?
Business Email Compromise doesn’t produce conspicuous digital traces. Instead, it lurks in plain view, utilizing clean frameworks, seemingly ordinary messages, and nuanced social manipulation.
Here’s why they often go unnoticed:
- Concealed motives – No malware involved, just links masquerading as everyday business.
- Reputable platforms – Hosted on services like OneDrive or Google Forms, which infrequently raise suspicions.
- Redirect sequences – Several transitions before the authentic phishing site surfaces.
- CAPTCHAs and blockers – Constructed to halt automated scripts and scanners.
- Human-centered approaches – Depends on social influence, rather than code execution.
- Context-aware communications – Customized with names, positions, and internal vernacular to evade doubt.
The Quickest Method To Identify A BEC Attack
When urgency is paramount, waiting hours for a conclusion simply isn’t feasible. Interactive sandboxes empower security teams to analyze dubious files or URLs in mere minutes, rather than hours or days.
Rather than depending on static evaluations or logs, analysts can observe the incident unfold in real-time, interact with it as a genuine user, and uncover the entirety of the threat.
To illustrate how this functions in practice, let’s examine a real-world phishing incident executed within ANY.RUN’s Interactive Sandbox.Examine analysis session with attack
This incident begins with a seemingly innocuous email containing a large green “Play Audio” button, a common enticement utilized by the Tycoon2FA phishing kit, one of the most prevalent threats in corporate settings today.
Here’s how the sandbox uncovers the complete chain:
1. Accessing The Email In A Secure VM
The email is uploaded to the sandbox and opened within an entirely isolated Windows setup. The analyst can securely click the “Play Audio” button to observe what occurs next, with no danger to their genuine system.

2. Tracking The Redirect Chain
Before initiating the analysis, users can activate Automated Interactivity, a feature in ANY.RUN that mimics genuine user actions, like pressing buttons, resolving CAPTCHAs, and following redirects.
Once activated, the sandbox automates these repetitive tasks, permitting analysts to monitor the complete attack trajectory without manual involvement.
In our instance, clicking the “Play Audio” button initiates a series of redirects, a classic evasion method employed to obscure the final phishing target.
Ultimately, a CAPTCHA challenge emerges, designed to obstruct automated scanners.

However, with Automated Interactivity active, ANY.RUN manages this effortlessly, resolving the CAPTCHA and proceeding with the analysis flow, conserving precious time and decreasing workload.
The sandbox arrives at the final phishing site within seconds, without requiring any manual effort, making it ideal for swift triage or high-volume alert management.
3. Arriving At The Final Phishing Site
After completing the CAPTCHA, the sandbox reaches a phony Microsoft login page; clean layout, familiar branding, but a dubious URL filled with random numbers and an absent favicon.
Warning signs a user might overlook but the sandbox discerns.

4. Revealing The Technical Information
Interactive sandboxes like ANY.RUN delineate the entire attack sequence so your team can comprehend precisely how the threat operates and where to address it.
Here are several details the sandbox disclosed in this session with Tycoon attack:
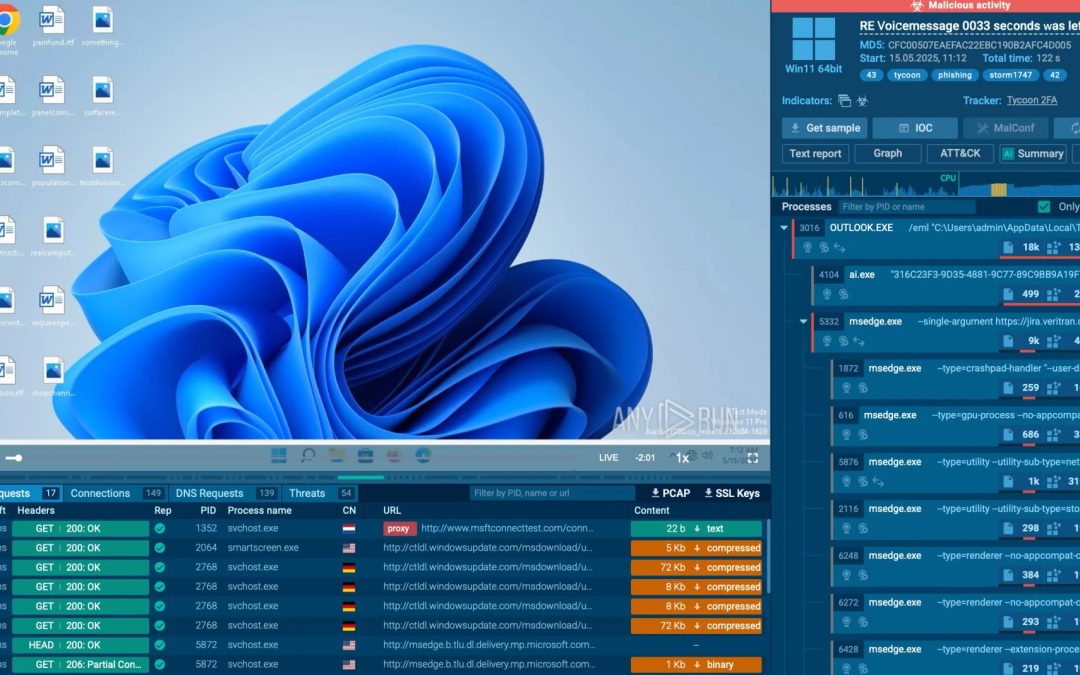
Complete Process Tree
In this instance, the process tree notably identified a suspicious browser process initiated after clicking the “Play Audio” button. It was marked as Phishing, with subprocesses indicating browser redirects and script executions.

The process hierarchy within ANY.RUN offers a detailed outline of how the phishing website was accessed, providing teams the insights necessary to trace multi-stage BEC threats that frequently conceal themselves in user behavior.
Network Requests: The sandbox recorded every HTTP/HTTPS request, encompassing redirect URLs and the ultimate phishing domain, a counterfeit Microsoft login page situated on a random, unbranded domain.

We observe how the sandbox unveils the entire attacker infrastructure associated with the Tycoon2FA kit, enabling teams to block harmful endpoints and comprehend the setup of the phishing operation.
Suricata Alerts: During the session, a Suricata rule was triggered: “PHISHING [ANY.RUN] Suspected Tycoon2FA’s Phishing-Kit Domain”.

This notification immediately confirms the threat with a distinct detection signature, expediting the decision-making process and allowing security teams to respond assuredly.
Tagged Verdict: ANY.RUN automatically classified the sample as associated with the Tycoon2FA phishing kit, recognizing the campaign behind the fraudulent login flow.

Removes uncertainty and guarantees prompt triage; even novice analysts can swiftly classify and report on the threat without extensive manual investigation.
How Interactive Sandbox Aids in Maintaining an Edge Against BEC Threats
Interactive sandboxing equips teams with the context, visibility, and speed necessary to identify and respond to Business Email Compromise threats prior to escalation.
Here’s how ANY.RUN offers that advantage:
- Real-time visibility into threat behavior
Observe the complete attack chain developing, from the initial lure to redirects, CAPTCHA challenges, and the conclusive phishing page, in real time.
- Quicker, more assured decisions
Receive an initial verdict in less than 40 seconds, accompanied by behavioral evidence to facilitate quicker triage and response.
- Automated Interactivity to lessen workload
Automate common user actions such as clicking buttons, solving CAPTCHAs, and following redirects. This conserves time and aids analysts in concentrating on higher-level decision-making.
- Cloud-based, no setup necessary
Examine files and URLs within a secure virtual environment from any location, without the need for infrastructure maintenance or local configuration.
- Centralized IOC collection
Accumulate and export domains, IPs, URLs, file hashes, and other indicators of compromise with one click, prepared for blocking, reporting, or enrichment.
- Built-in threat classification
Obtain immediate context with labeled processes, triggered Suricata rules, and campaign-level tagging (e.g., Tycoon2FA) to expedite identification.
- Supports all analyst skill tiers
Whether it’s a novice SOC analyst or a seasoned threat hunter, ANY.RUN provides an intuitive interface and detailed reporting to assist in investigation, learning, and collaboration.
- Enhances security workflows
Minimizes alert fatigue, shortens incident response duration, and assists teams in prioritizing genuine threats over false positives.
Equip your team with the solution to detect sophisticated phishing threats in real time, reduce analyst workload, and respond with assurance: Join ANY.RUN to explore its full features for 14 days →The article Business Email Compromise Attacks: How To Detect Them Early appeared first on Cyber Security News.
“`