“`html
ArmouryLoader emerged onto the threat scene in late 2024 after seizing the export table of ASUS’s Armoury Crate utility, transforming a reputable gaming application into an entry vector for complex malware operations.
Since that time, cybersecurity teams have observed a consistent rise in incidents where the loader discreetly bypasses endpoint monitoring, decrypts its payload within GPU memory, and activates anything from CoffeeLoader to SmokeLoader without placing any files on disk.
.webp)
The loader’s capability to identify OpenCL-compatible devices, merge privilege elevation with sophisticated obfuscation, and forge call stacks has rendered it a preferred choice for financially driven threat actors targeting both consumer and corporate settings.
Cybercriminals typically deliver the compromised ArmouryA.dll through spear-phishing archives or infiltrated software repositories.
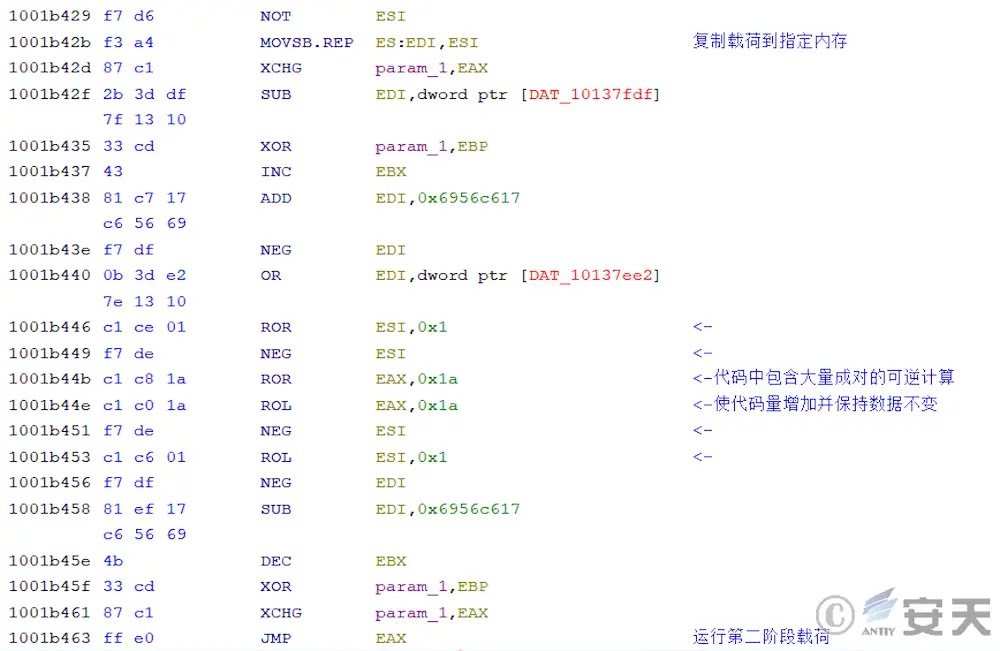
Upon side-loading the malicious DLL, execution proceeds to Stage 1—an array of reversible arithmetic operations crafted to pad disassembly listings while keeping registers unaltered.
.webp)
In mere seconds, Stage 2 creates a new thread, decrypts the subsequent PE stub, and transitions execution to Stage 3, where an OpenCL kernel carries out XOR operations on ciphertext blocks entirely within the GPU, evading sandbox hooks that monitor CPU-related API calls.
.webp)
4hou analysts observed that the loader’s GPU reliance requires many automated sandboxes to hit dead ends since they provide virtualized, non-accelerated graphics adapters.
The loader’s influence is far-reaching: remote working endpoints receive second-stage Trojans, SOCs grapple with obscure call traces, and incident responders face ongoing tasks that reinstall freeBuffer hijacks after each reboot.
Digital signatures embedded in the rogue DLL contain the legitimate “ASUSTeK COMPUTER INC.” publisher field, further facilitating social-engineering tactics targeting non-technical users who rely on visible certificates.
Persistence Strategies: Scheduled Tasks That Won’t End
While obfuscation and GPU-side decryption capture the majority of attention, ArmouryLoader’s persistence layer is the subtle force that ensures prolonged access.
Stage 5 initiates by querying TokenElevationType and CheckTokenMembership to ascertain whether the current context boasts administrative privileges.
If affirmed, the loader replicates itself to %PROGRAMDATA%ArmouryAIOSDK.dll, assigns System, Hidden, and Read-Only attributes, and modifies the file’s ACL so that even local administrators encounter a “Deny Delete” entry.
The following code snippet—taken from the fifth-stage PE—illustrates how those rights are enforced:
pList.grfAccessPermissions =
DELETE | FILE_WRITE_DATA | FILE_APPEND_DATA |
FILE_WRITE_EA | FILE_WRITE_ATTRIBUTES;
pList.grfAccessMode = DENY_ACCESS;
SetEntriesInAclW(1, &pList, NULL, &newAcl);
SetNamedSecurityInfoW(L"%ProgramData%ArmouryAIOSDK.dll",
SE_FILE_OBJECT, DACL_SECURITY_INFORMATION,
NULL, NULL, newAcl, NULL);If high integrity isn’t accessible, Stage 5 degrades smoothly, dropping the DLL into %LOCALAPPDATA% and still applying identical attribute-hardening. Regardless of path, it invokes schtasks.exe (or, in newer versions, the Task Scheduler COM API) to create an “AsusUpdateServiceUA” job.
In elevated contexts, the task executes on logon with the /RL HIGHEST flag; otherwise, it repeats every 30 minutes under the current user.
Figure 2-5 in the original report (“AsusUpdateServiceUA Properties.png”) illustrates the job set to initiate at each sign-in, solidifying the foothold.
Subsequent variations fully bypass schtasks.exe, invoking ITaskDefinition::RegisterTaskDefinition so that EDR policies monitoring command-line artifacts detect nothing unusual.
A final touch guarantees stealth: ArmouryLoader rewrites the PEB’s ImagePathName and the corresponding LDR_DATA_TABLE_ENTRY strings to “explorer.exe” prior to utilizing CMLuaUtil to relaunch itself with complete administrative rights.
Any security tool conducting surface-level process name checks thus presumes the privilege escalation stemmed from the Windows shell.
By linking manipulated digital signatures, encrypted GPU workloads, and ACL-hardened scheduled tasks, ArmouryLoader provides a resilient, low-noise delivery channel that is likely to remain appealing to attackers until defenders strengthen GPU telemetry and limit task-registration APIs across systems.
“`