The DMARC protocol serves as an email authentication method that aids domain owners in safeguarding against unauthorized activities such as “email spoofing” and “phishing attempts.”
Through the utilization of existing protocols like “SPF” and “DKIM,” DMARC empowers domain owners to establish guidelines within their “DNS records” that determine the actions receiving servers should take upon receiving emails that do not pass authentication checks.
A recent discovery by Barracuda researchers revealed that North Korean APT hackers are actively taking advantage of misconfigurations in DMARC to carry out phishing attacks.
Exploitation of DMARC Misconfigurations by Hackers
The cyber realm was recently shaken by the highly sophisticated exploitation of email security weaknesses by the North Korean hacking group, Kimsuky. They specifically targeted vulnerabilities in misconfigured DMARC protocols.
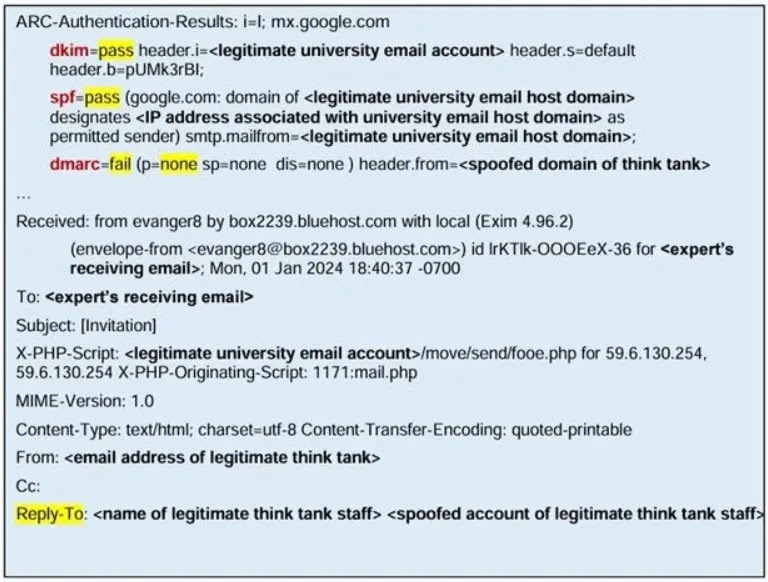
Operating under the supervision of North Korea’s Reconnaissance General Bureau, this APT group initiated strategic spear-phishing campaigns by bypassing feeble email authentication systems, including the checks for “SPF” and “DKIM.”
Their focal point was to infiltrate “think tanks,” “media entities,” and “educational institutions.”
These targets were approached through the creation of malicious emails that appeared legitimate due to crafty “domain spoofing” tactics.
Due to numerous organizations applying inadequate DMARC policies (typically set to ‘none’ or incorrectly configured) as opposed to implementing strict ‘quarantine’ or ‘reject’ settings, these malevolent emails were able to bypass standard security measures.
This oversight in security enabled “Kimsuky” to deliver potentially harmful content directly into users’ inboxes.
It has come to light that their primary focus lies in obtaining sensitive information related to “foreign relations” and “nuclear issues.”
This incident underscores how inaccuracies in email authentication protocols can give rise to significant security vulnerabilities, even within what seems like “well-fortified systems.”
The strategy employed by the Kimsuky group in executing phishing attacks involves a calculated two-phase email strategy.
Initially, they dispatch authentic-looking emails posing as “reputable institutions” to establish trust with their targets.
Subsequently, after gaining trust, they proceed with the “second phase” by sending out “follow-up emails” containing “harmful payloads,” either through “infected attachments” or “malicious links.”
Their attacks become notably potent when they successfully infiltrate valid email systems, which enables them to circumvent crucial email authentication protocols.
In an instance, they invited targets to a “North Korea policy conference” via a “spear-phishing email” that managed to pass ‘SPF’ and ‘DKIM’ verification because they exploited a legitimate email system that had been hacked.
Many entities misuse the functionalities of “DMARC,” particularly by opting for a “monitor-only” policy that solely logs threats without actively thwarting them.
This poses a severe security risk to operational email addresses, leading to vulnerabilities where illicit and harmful spam emails can slip through undetected.
Suggestions
Outlined below are some key recommendations:-
- Prioritize “quarantine” or “reject” for unsuccessful emails.
- Deploy AI-powered email protection to identify sophisticated threats that may elude detection by DMARC.
- Conduct regular phishing drills for preparedness.
The post North Korean APT Hackers Exploiting DMARC Misconfigs For Phishing Attacks appeared first on Cyber Security News.