“`html
Google-owned Mandiant has made public a thorough dataset of Net-NTLMv1 rainbow tables, signifying a notable intensification in illustrating the security threats of outdated authentication protocols.
This release conveys an urgent warning: organizations must promptly transition away from Net-NTLMv1, an obsolete protocol that has been deemed cryptographically compromised since 1999 and widely recognized as insecure since at least 2012.
In spite of two decades of security alerts, Mandiant consultants are still detecting Net-NTLMv1 in operational enterprise settings, indicating that organizational inertia is a significant obstacle to remediation.

The importance of this release is in significantly reducing the operational threshold for credential retrieval. Previously, taking advantage of Net-NTLMv1 necessitated either uploading sensitive authentication data to external services or relying on costly specialized hardware for brute-force assaults.
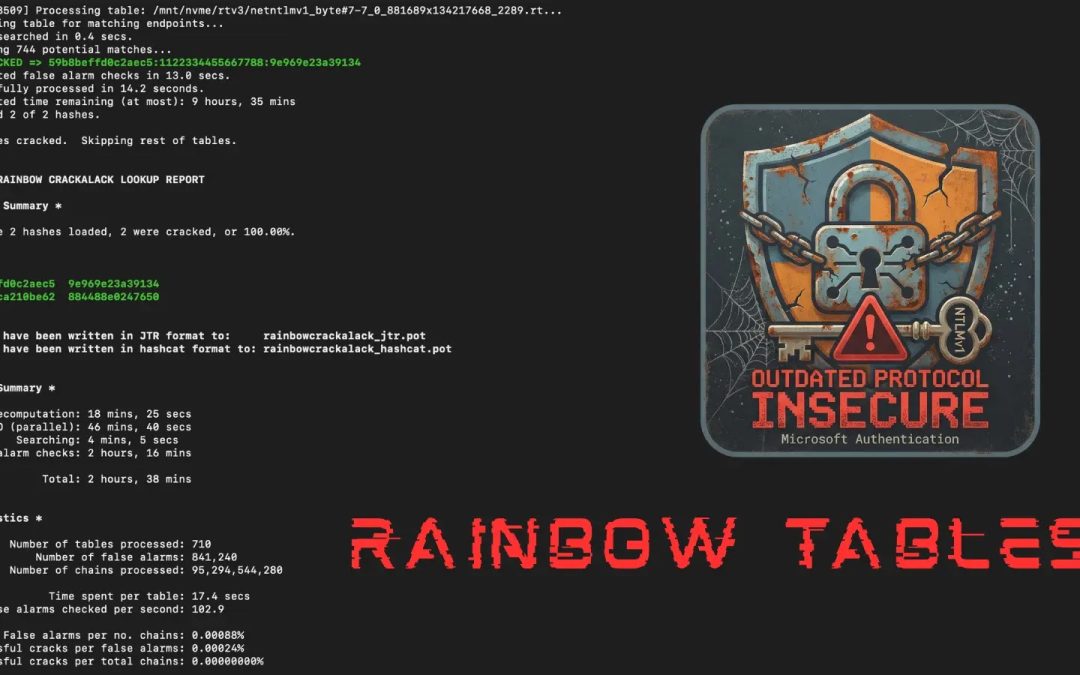
Mandiant’s dataset now allows security professionals to recover authentication keys in less than 12 hours utilizing consumer-grade hardware priced under $600 USD. This newfound accessibility shifts Net-NTLMv1 from a theoretical risk to a practical attack avenue available to a substantially larger pool of threat actors.
Rainbow Tables Enabling NTLMv1 Admin Hack
The weakness arises from Net-NTLMv1’s dependence on a known plaintext attack (KPA) approach. When an attacker secures a Net-NTLMv1 hash without Extended Session Security (ESS) for the known plaintext value of 1122334455667788, they may use cryptographic strategies to retrieve the key material, which corresponds to the password hash of the authenticating Active Directory object.
The attack sequence usually starts with manipulating authentication against highly privileged entities, such as domain controllers, employing tools like PetitPotam or DFSCoerce to compel incoming connections.
Once acquired, attackers convert Net-NTLMv1 hashes into DES components using utilities like ntlmv1-multi, then utilize Mandiant’s rainbow tables with tools such as RainbowCrack or RainbowCrack-NG to retrieve the DES keys.
The final key element can be computed or referenced using specialized tools, reconstructing the complete NT hash for credential compromise.
A frequent escalation trajectory includes retrieving a domain controller machine account hash, which then enables DCSync attacks to compromise any account within Active Directory.
Rainbow tables constitute a time-memory trade-off method first suggested by Martin Hellman in 1980, with formal development presented by Philippe Oechslin in 2003.
Hashcat introduced support for cracking DES keys using known plaintext in August 2016, further democratizing Net-NTLMv1 exploitation. Mandiant’s release merges Google Cloud’s computational power with frontline security knowledge to eradicate an entire category of authentication threats on a large scale.

The dataset can be accessed through the Google Cloud Research Dataset portal or via gsutil commands. SHA512 checksums facilitate dataset integrity verification, and the security community has already developed derivative implementations optimized for both CPU and GPU processing.
Attackers utilize Responder with the –lm and –disable-ess flags, establishing authentication to the fixed value 1122334455667788 to enforce Net-NTLMv1 negotiation.

Organizations can detect this behavior by filtering Windows Event Log Event ID 4624 (“An Account was successfully logged on”) for the “Authentication Package” field, alerting when “LM” or “NTLMv1” values surface.
Immediate mitigation requires deactivating Net-NTLMv1 across the organization. Windows systems should be configured to “Send NTLMv2 response only” via Local Security Settings or Group Policy, notably through “Network Security: LAN Manager authentication level” settings.
Nonetheless, organizations need to be aware that local system configurations permit attackers with administrative access to downgrade settings post-compromise, necessitating ongoing monitoring and detection strategies beyond mere policy enforcement.
The launch of Mandiant’s rainbow tables signifies a pivotal moment in Net-NTLMv1 security dialogues. What was once an academic issue has evolved into a tangible, accessible attack vector that demands immediate organizational focus and comprehensive remediation strategies.
“`