“`html
LAS VEGAS — At DEF CON 33 cybersecurity conference, researchers Yair and Shahak Morag from SafeBreach Labs revealed a novel category of denial-of-service (DoS) attacks, termed the “Win-DoS Epidemic.”
The pair shared their discoveries, which encompass four fresh Windows DoS vulnerabilities and an additional zero-click distributed denial-of-service (DDoS) issue.
The identified vulnerabilities, all classified as “uncontrolled resource consumption,” are:
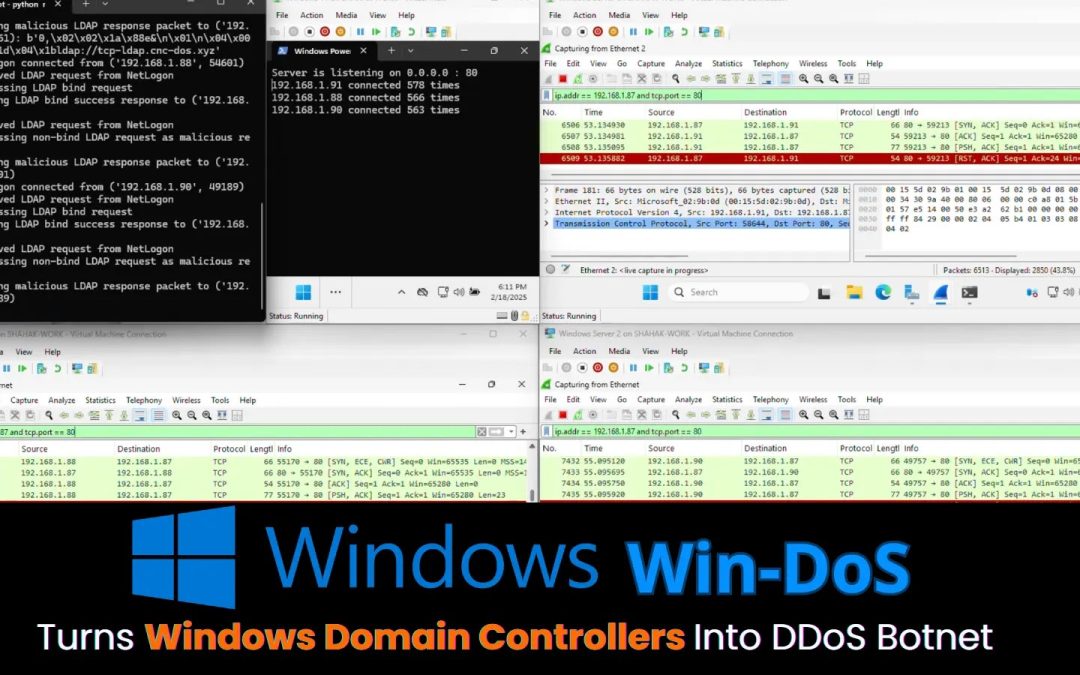
- CVE-2025-26673 (CVSS 7.5): A high-severity DoS vulnerability in Windows LDAP.
- CVE-2025-32724 (CVSS 7.5): A high-severity DoS vulnerability in Windows LSASS.
- CVE-2025-49716 (CVSS 7.5): A critical DoS vulnerability in Windows Netlogon.
- CVE-2025-49722 (CVSS 5.7): A medium-severity DoS vulnerability in the Windows Print Spooler, necessitating an authenticated attacker on a neighboring network.
The research highlights how attackers can incapacitate any Windows endpoint or server, encompassing vital Domain Controllers (DCs), and even weaponize public DCs to fabricate a vast DDoS botnet.
“We introduce the “Win-DoS Epidemic” – DoS instruments leveraging four fresh Win-DoS and one Win-DDoS zero-click vulnerabilities! Crash any Windows endpoint/server, comprising DCs, or mobilize a botnet via public DCs for DDoS. The epidemic has commenced,” researchers proclaimed.
The Perils of DoS on Domain Controllers
Domain Controllers serve as the foundation of most organizational networks, managing authentication and consolidating user and resource administration.
A successful DoS assault on a DC can immobilize an entire organization, obstructing users from logging in, accessing resources, or completing routine operations.
The researchers’ work enhances their prior finding, the LdapNightmare vulnerability (CVE-2024-49113), which was the inaugural public DoS exploit for a Windows DC. These new discoveries significantly expand this menace, transcending merely LDAP to exploit other core Windows services.
A Novel Botnet Exploiting Public Infrastructure
The most disconcerting revelation is a new DDoS methodology, which the researchers dubbed Win-DDoS. This assault utilizes a flaw in the Windows LDAP client’s referral system.
During standard operations, an LDAP referral directs a client to an alternate server to fulfill a request. Yair and Morag identified a method to manipulate this procedure, allowing them to redirect DCs to a victim server, and crucially, they engineered a way for the DCs to perpetually execute this redirection.
This behavior permits an assailant to harness the vast power of tens of thousands of public DCs globally, transforming them into a colossal, free, and untraceable DDoS botnet.
The attack necessitates no specialized infrastructure and leaves no forensic evidence, as the malicious activity emanates from the compromised DCs, not the perpetrator’s device.
This technique signifies a decisive shift in DDoS assaults, enabling high-bandwidth, high-volume strikes without the usual expenses or risks tied to establishing and maintaining a botnet.
Exploiting RPC for System Failures
Alongside the DDoS botnet, the researchers concentrated on the Remote Procedure Call (RPC) framework, a key component of Windows for inter-process communication.
RPC servers are prevalent in the Windows landscape and often feature extensive attack surfaces, especially those that do not mandate authentication.
The SafeBreach team uncovered that by exploiting security weaknesses in RPC bindings, they could continuously target the same RPC server from a solitary system, effectively circumventing standard concurrency restrictions.
This approach enabled them to identify three new zero-click, unauthenticated DoS vulnerabilities that can incapacitate any Windows system—servers and endpoints alike.
They further discovered another DoS flaw that can be leveraged by any authenticated user present on the network.
These vulnerabilities challenge common assumptions that internal systems are secure from abuse without total compromise, illustrating that even minimal access on a network can trigger extensive operational disruption.
The researchers have launched a suite of tools, collectively termed “Win-DoS Epidemic,” that exploit these five new vulnerabilities. These tools can be employed to crash any unpatched Windows endpoint or server remotely, or to orchestrate a Win-DDoS botnet using public DCs.
These revelations emphasize the urgent necessity for organizations to reevaluate their threat models and security strategies, especially concerning internal systems and services like DCs.
Microsoft has since issued patches for the LdapNightmare vulnerability, but the recent findings spotlight the persistent need for vigilance and continual security validation.
“`