Cyber Security
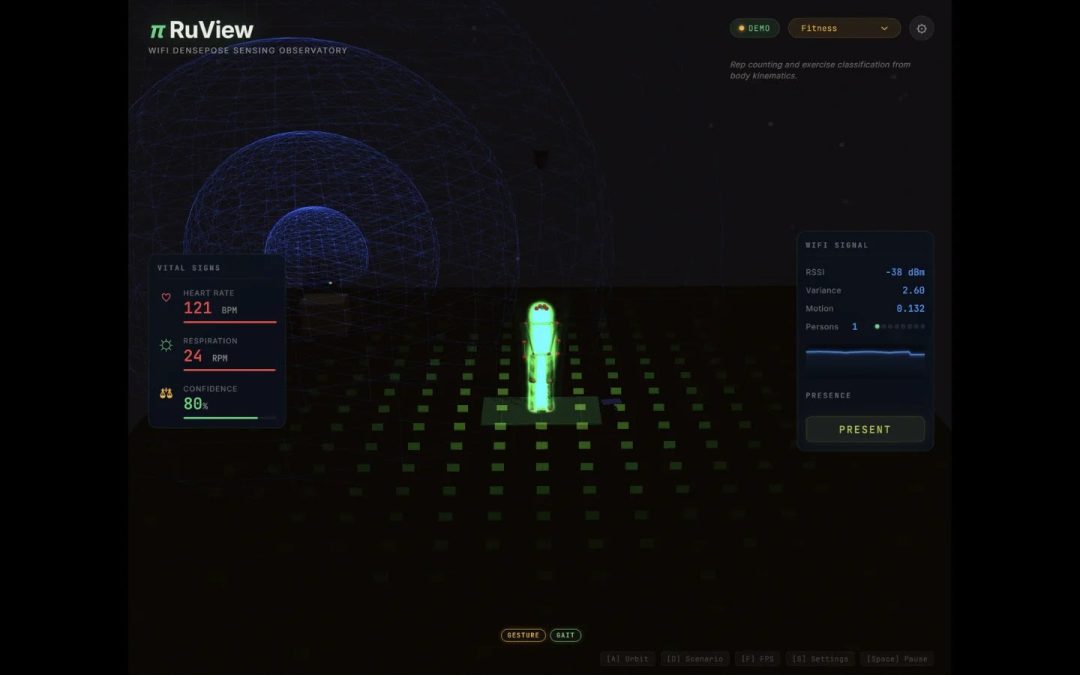
“`html A novel open-source edge AI system named π RuView is transforming standard WiFi infrastructure into a through-wall human-detection platform identifying body posture, vital signs, and movement patterns without any cameras, thus raising significant security...

Cyber Security
“`html Zero-Click Command Injection AVideo Platform Allows Stream Hijacking A severe flaw in AVideo, a popular open-source video hosting and streaming solution, has been identified. Labeled as CVE-2026-29058, this zero-click vulnerability holds the highest...

Cyber Security
“`html Cybersecurity analysts have discovered a fresh wave of ClickFix assaults that now utilize Windows Terminal to deliver malicious payloads directly onto victim systems. In contrast to previous iterations of this social manipulation tactic, which depended on...

Cyber Security
“`html GPT-5.4 Launched On March 5, 2026, OpenAI unveiled GPT-5.4, its most advanced and effective frontier model thus far, amalgamating sophisticated reasoning, programming, and agentic workflows into one cohesive system. This model is being deployed across...

Cyber Security
“`html Microsoft, Europol, and collaborators have dismantled the Tycoon 2FA phishing-as-a-service (PhaaS) network, confiscating 330 domains utilized for credential theft and MFA evasion. This collaborative initiative disrupts a service that has been operational...

Cyber Security
“`html Windows 11 23H2 to 25H2 Upgrade A persistent flaw in Windows 11 in-place upgrades is allegedly erasing vital 802.1X wired authentication settings, leaving corporate workstations entirely disconnected until manual actions are taken. System administrators...

Cyber Security
“`html Chrome Gemini Vulnerability A critical severity security flaw has been identified in Google Chrome’s embedded Gemini AI assistant, putting users at risk of unauthorized access to their camera and microphone, theft of local files, and phishing schemes, all...

Cyber Security
“`html AWS Power Outage On March 1, 2026, a significant power interruption in the AWS me-central-1 (Middle East) region was triggered by an unusual physical occurrence where external objects collided with a data center, igniting sparks and a fire. This incident...

Cyber Security
“`html A significant zero-interaction flaw in OpenClaw, one of the swiftly expanding open-source AI agent frameworks, has been identified by Oasis Security experts, enabling any harmful website to quietly take complete command of a developer’s AI agent...

Cyber Security
“`html The U.S. administration has executed extraordinary measures against the domestic AI enterprise Anthropic, instructing every federal department to promptly halt the usage of its AI model Claude and formally classifying the organization as a supply chain...











