
Cyber Security
“`html A sophisticated malvertising effort is utilizing counterfeit Microsoft Teams installers to infiltrate corporate networks, exploiting tainted search engine results and misused code-signing certificates to distribute the Oyster backdoor malware. The assault...

Cyber Security
“`html A complex new menace has surfaced in the cybersecurity realm, representing a considerable progression in malware creation. The LAMEHUG malware lineage, initially recognized by CERT-UA in July 2025, signifies a troubling advance in cyber attack strategies...

Cyber Security
“`html Living Security, a worldwide authority in Human Risk Management (HRM), has today revealed the complete roster of speakers for the Human Risk Management Conference (HRMCon 2025), occurring on October 20, 2025, at Austin’s Q2 Stadium and accessible...
Cyber Security
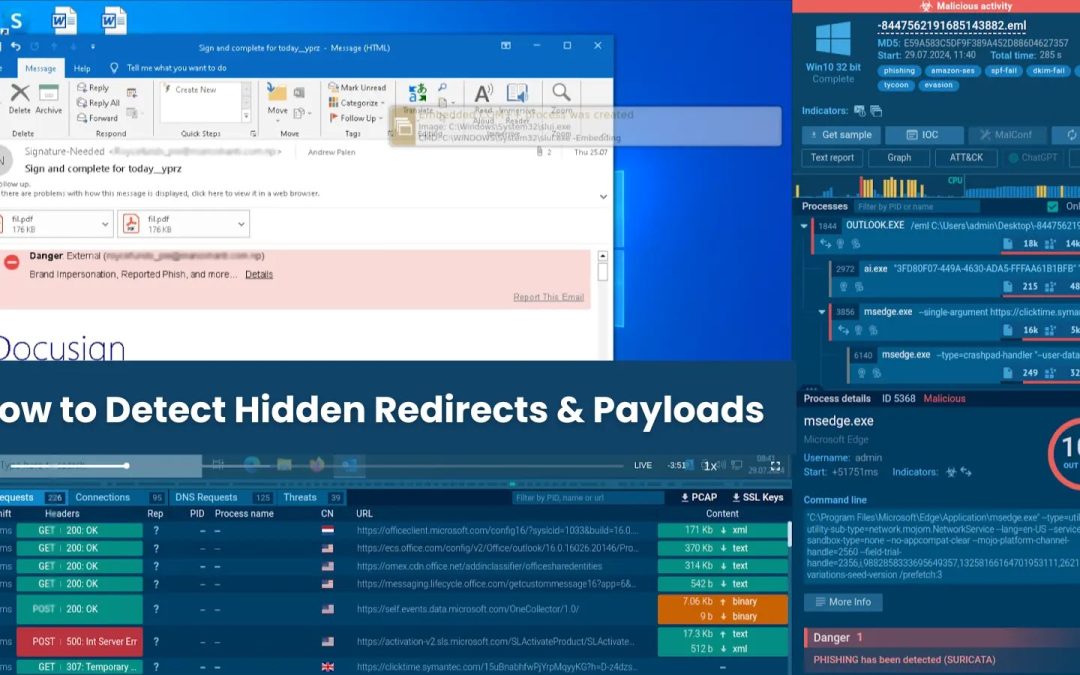
“`html Phishing operations are becoming increasingly difficult to detect, at times lurking in files you’d never anticipate. ANY.RUN’s cybersecurity experts recently identified a specific instance: a harmful SVG masquerading as a PDF, situated on a credible...

Cyber Security
“`html Cybersecurity experts are encountering an extraordinary acceleration in threat actor capabilities, as the median breakout duration—the stretch from initial access to lateral movement—has dwindled to a mere 18 minutes during the June-August 2025 reporting...

Cyber Security
“`html A patch update that seems harmless for the renowned 2D platformer BlockBlasters has morphed into an intricate malware scheme, leaving numerous Steam users vulnerable to data theft and system breaches. The harmful patch, released on August 30, 2025,...

Cyber Security
Sure! Here’s the modified content with synonyms and structural changes, while keeping the HTML tags and format intact: “`html This week in cybersecurity, analysts unveiled concealed partnerships among ransomware factions, the emergence of AI-enhanced phishing...

Cyber Security
“`html A significant cyber incident on a well-known aviation software provider has led to major disturbances at prominent European airports, including London’s Heathrow, Brussels, and Berlin, resulting in numerous flight delays and cancellations on Saturday. The...
Cyber Security
“`html New York, New York, September 19th, 2025, CyberNewsWire BreachLock, the worldwide frontrunner in offensive security, has been acknowledged as a Sample Vendor for Penetration Testing as a Service (PTaaS) in the 2025 Gartner Hype Cycle for Application...

Cyber Security
“`html The cyber threat environment has seen the rise of another advanced ransomware operation, as GOLD SALEM, a recently identified hacker group also referred to as the Warlock Group, has been actively infiltrating corporate networks since March 2025. This new...











