
Cyber Security
“`html A recently identified major flaw in the Next.js framework permits attackers to incapacitate self-hosted servers with a solitary HTTP request, necessitating minimal resources for execution. Unearthed by analysts at Harmony Intelligence, the...

Cyber Security
“`html Horsham, United Kingdom, November 25th, 2025, CyberNewsWire Detego Global, the firm behind the acclaimed Unified Digital Forensics Platform, is excited to unveil the Detego Case Manager for DFIR, a robust, specifically developed platform aimed at...

Cyber Security
“`html NVIDIA has revealed two severe code injection vulnerabilities impacting its Isaac-GR00T robotics framework. The vulnerabilities, identified as CVE-2025-33183 and CVE-2025-33184, are present within Python modules and may enable authenticated attackers to...

Cyber Security
“`html The Cybersecurity and Infrastructure Security Agency (CISA) is encouraging organizations to promptly rectify a critical security vulnerability in Oracle Identity Manager following reports of active exploitation. The flaw, noted as CVE-2025-61757, enables...

Cyber Security
“`html A complex supply chain assault has allegedly breached data across numerous organizations, connecting the incident to a significant integration between the customer success platform Gainsight and the CRM powerhouse Salesforce. The infamous hacking group...

Cyber Security
“`html The cybersecurity behemoth CrowdStrike has verified the dismissal of an insider who reportedly leaked sensitive details of internal systems to a well-known hacking group. The occurrence, which emerged late Thursday and into Friday morning, involved the...

Cyber Security
“`html A significant remote code execution vulnerability in Microsoft’s Windows Graphics Component permits attackers to gain control of systems by utilizing specially crafted JPEG files. With a CVSS rating of 9.8, this vulnerability represents a critical risk to...
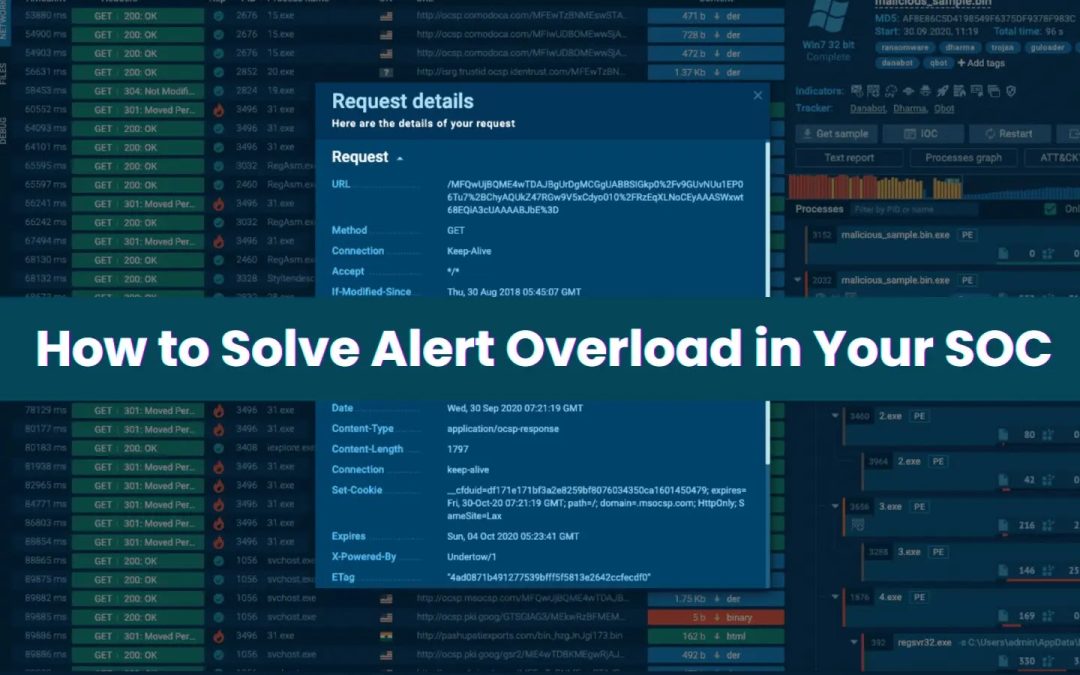
Cyber Security
“`html Your SOC produces numerous alerts each day. A significant portion of these are minor, repetitive, or erroneously triggered. While this may appear to be a technical dilemma, it is fundamentally a business challenge. Each Alert Has a Cost When analysts are...

Cyber Security
“`html Cloudflare issued a detailed report explaining the origins of a significant network disruption that hindered global internet traffic for multiple hours, impacting millions of users and various platforms. The disruption, which commenced at 11:20 UTC,...

Cyber Security
“`html IBM has issued significant security patches that address two critical vulnerabilities in its AIX operating system, which could permit remote intruders to execute arbitrary commands on vulnerable systems. Both weaknesses arise from inadequate process...











