“`html
Security Operations Centers (SOCs) and Managed Security Service Providers (MSSPs) function at the cutting edge of cybersecurity, assigned with safeguarding entities from increasingly complex hazards.
As adversaries hone their strategies, the necessity for ongoing skill enhancement, especially through practical malware analysis training, has become crucial.
This program examines how experiential training initiatives boost the proficiency of SOC and MSSP teams, empowering them to identify, scrutinize, and eliminate advanced threats with accuracy.
Malware Analysis Training For SOC & MSSP Teams
Contemporary SOCs and MSSPs act as consolidated centers for threat identification and response. SOCs consist of internal squads that supervise an organization’s networks, endpoints, and systems round the clock, while MSSPs deliver these services to numerous clients, frequently overseeing varied IT environments. Both depend on tiered analyst frameworks:
- Tier 1 analysts screen alerts, confirm incidents, and escalate intricate cases.
- Tier 2 analysts delve deeper into investigations, utilizing threat intelligence to give context to threats.
- Threat hunters actively seek out indicators of compromise (IOCs) and elusive adversaries.
These teams endure continuous pressure to diminish mean time to detect (MTTD) and mean time to respond (MTTR). Nevertheless, automated instruments alone are insufficient to unravel the complexities of contemporary malware, which frequently employs obfuscation, polymorphism, or zero-day vulnerabilities.
Cybersecurity is an ever-evolving domain where stagnation equals susceptibility. Ongoing education ensures analysts remain skilled in recognizing new attack vectors, such as fileless malware or supply chain disruptions. For SOCs and MSSPs, this entails
| SOC Tasks (In-House, Organization-Focused) | MSSP Tasks (Multi-Client, Service-Driven) |
|---|---|
| Investigate endpoint infections to trace malware entry and behavior | Analyze malware artifacts from multiple client environments |
| Examine suspicious files and email attachments flagged by EDR/XDR | Identify zero-day threats across diverse networks |
| Correlate logs and IOCs to confirm ongoing attacks | Augment threat intelligence feeds with behavior-based indicators |
| Refine detection rules (e.g., YARA, SIEM correlation) based on malware TTPs | Create client-specific detection content (custom alerts, signatures) |
| Support incident response playbooks with updated malware knowledge | Prioritize alerts and escalations using malware behavior context |
| Simulate attack scenarios to test internal defenses against known malware | Provide thorough incident reports elucidating malware operations to clients |
| Conduct post-incident forensic analysis for internal audits and reporting | Actively hunt for new threats across managed client infrastructure |
What SOC and MSSP Teams Have in Common
In spite of the variations in their operational models, both SOC and MSSP teams possess several fundamental needs concerning effective malware examination and threat response:
- Hands-on Training with Real-World Malware:
Both teams require tangible experience with authentic malware examples, not merely theoretical or simulated threats. This exposure aids analysts in recognizing genuine attack patterns and behaviors. - Visibility into Malware Behavior:
Analysts must be capable of witnessing how malware functions in a controlled setting, encompassing process trees, file system modifications, registry alterations, and network activities. This visibility is vital for precise threat appraisal and response. - Rapid, Precise Triage and Threat Validation:
Serving either a single organization or multiple clients, both SOC and MSSP teams must rapidly ascertain which alerts represent actual threats and which are false alarms. Hands-on analysis skills promote more efficient and confident triage. - Utilization of Secure, Interactive Analysis Platforms:
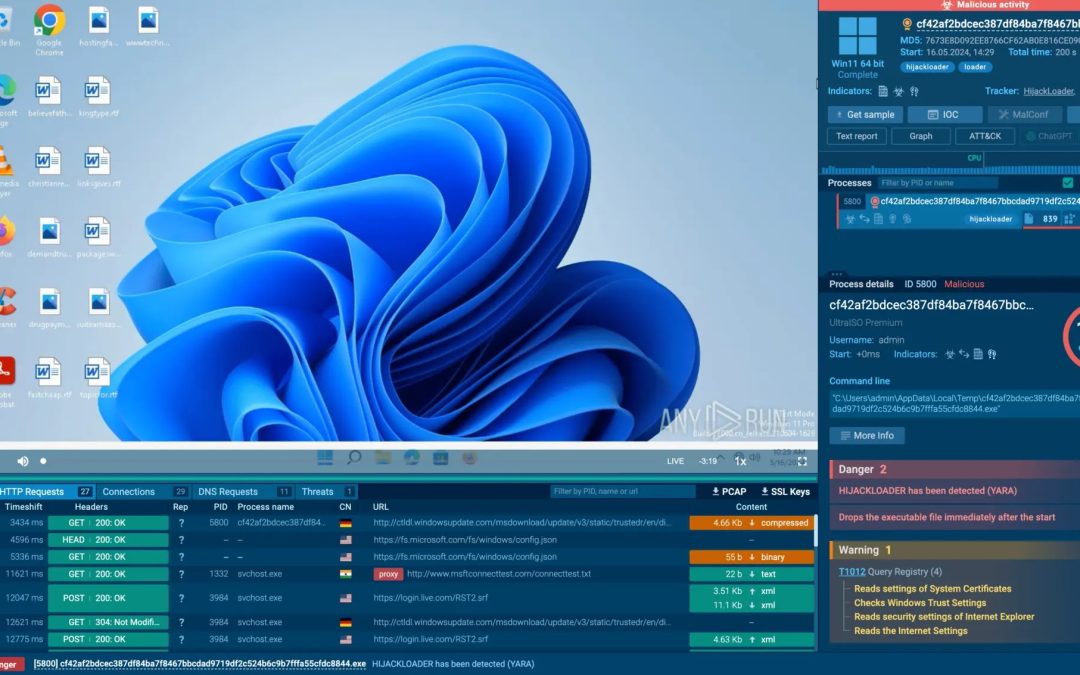
Protected, sandboxed environments like ANY.RUN’s Security Training Lab facilitate safe malware investigations without jeopardizing production systems, aiding both educational and operational requirements. - Continuous Improvement in Detection and Response:
In-depth
“““html- Comprehension of Malware:
Awareness of malware allows teams to enhance detection protocols, develop personalized signatures, and revise incident response playbooks, resulting in swifter identification and alleviation of threats. - Sync with Current Threat Patterns:
Consistent exposure to emerging and transforming malware guarantees that both SOC and MSSP analysts remain updated, modifying their defenses to the latest strategies employed by adversaries.
Malware creators continuously adjust their strategies, techniques, and methodologies (TTPs). For instance, ransomware factions now utilize living-off-the-land binaries (LOLBins) to avoid detection. Frequent training equips analysts to spot these trends and amend detection protocols ahead of time.
A significant number of junior analysts lack practical experience with real-world malware. Practical training hastens proficiency by immersing them in genuine attack scenarios, such as analyzing phishing email attachments or scrutinizing ransomware payloads.
Multi-disciplinary training encourages knowledge exchange between SOC layers and MSSP clients. For example, analysts proficient in behavioral analysis can more effectively convey malware’s effects to stakeholders, fostering informed decision-making.
With ANY.RUN malware analysis training, participants gain unrestricted access to the sandbox and a tailored collection of new malware samples contributed by ANY.RUN’s vast global user community of 15,000 corporate security teams.

Illustrative examples are contrasted with insights acquired from inspecting live malware samples. Practical training arenas, like sandboxes, enable analysts to:
Analysts monitor activities such as registry changes, network callbacks, and payload deployments by executing suspicious files in isolated environments. For example, a sample might try to connect to a command-and-control (C2) server located at
147[.]185.221.26, an IP associated with AsyncRAT and Xworm operations.Hands-on activities instruct analysts on how to formulate YARA rules and SIEM correlations based on identified TTPs. For instance, pinpointing a malware family that encrypts files with a certain extension necessitates awareness of its static attributes (e.g., cryptographic hashes) and dynamic behaviors (e.g., process injection).
Reverse engineering and memory analysis are vital for dissecting complex threats. Training programs that incorporate debugging utilities (e.g., x64dbg) and memory examination frameworks (e.g., Volatility) empower analysts to uncover concealed payloads or anti-analysis techniques.
ANY.RUN’s Security Training Lab illustrates how immersive training enhances SOC and MSSP capabilities. Key attributes include:
A 30-hour syllabus encompasses malware analysis essentials, from fundamental triage to advanced reverse engineering. Video presentations, quizzes, and practical tasks guarantee thorough skill enhancement.
- This 30-hour interactive digital course encompasses written content, video lessons, assignments, and evaluations, organized into ten modules addressing essential aspects of malware analysis.
- A holistic training atmosphere utilizing authentic malware variants.
- Tools that replicate genuine SOC environments.
- Support from cross-industry collaboration.

Course Overview - Comprehension of Malware:
“`

.png%0D%0A)