The realm of cyber dangers is complex and constantly evolving. Threat perpetrators are consistently enhancing their techniques, and fresh variants of data-stealing malware frequently emerge.
Data theft tools are straightforward to use, cost-effective, and have minimal entry barriers, rendering them extremely perilous even for less-experienced threat actors.
A recent variation, named PureLogs, is a 64-bit data-collecting software created in C# and packages its components into multiple phases utilizing the.NET Reactor packer.
This data thief possesses the capability to procure private information through the Chrome browser, a trait it shares with only a handful of other malware variants, including Lumma, Vidar, and Meduza.
In the current landscape of threats, it is crucial for cybersecurity professionals to stay informed about emerging variants like PureLogs.
PureLogs- An Economical Data Thief
In 2022, PureLogs was initially available for purchase on clandestine markets and has since been promoted on numerous underground forums. It also maintains an account and a dedicated marketplace on the clearnet.
Direct purchases are no longer facilitated on this website, but it directs potential customers to a Telegram bot for assistance and sales inquiries. Priced starting from $99 for a month, $199 for three months, $299 for a year, and $499 for a lifetime membership, PureLogs stands as one of the most budget-friendly data theft tools on the market.
In addition to the data-stealing software, its creator is vending other “wares” that equip threat actors with access to supplementary resources such as a digital currency miner, utilities for substituting clipboards, a botnet capable of executing DDoS attacks, and a concealed Virtual Network Computing client.
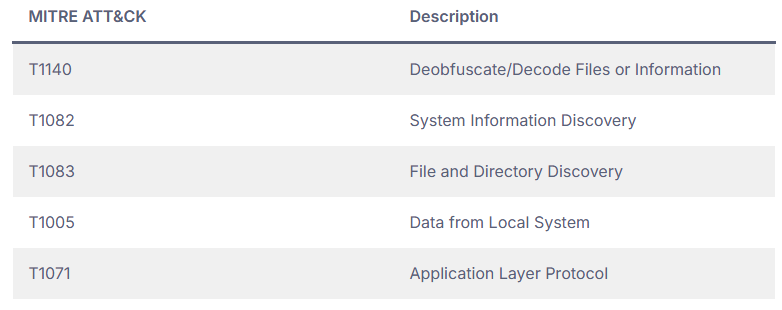
Per the Flashpoint Intel Team report, PureLogs functions through three phases. The first phase concerns the loading and execution. Subsequently, the second stage appears to oversee anti-sandbox assessments and network setups before loading the ultimate data-stealing component.
The data-stealing code is located in the third stage. PureLogs acquires the subsequent details:
- Internet browsing records
- Browser extensions in Chrome, Edge, and Opera
- Cryptocurrency wallet applications
- Desktop applications
- Information about the victim’s device
PureLogs can retrieve folders, files based on extensions, or files named and located in specific directories. It can also fetch and operate additional payloads from an external URL.
During configuration, PureLogs users have the choice to forward the pilfered data to Telegram. The Telegram messages from the PureLogs interface contain insights on the victim, the quantity of purloined data, the captured screenshot, and the comprehensive log that is downloadable.
Hence, to shield enterprises against this emerging menace, security teams must have immediate access to substantial threat intelligence.
The article PureLogs, Low Cost Data Thief Targeting Chrome Browser was originally published on Cyber Security News.