Flax Typhoon, a malevolent cyber actor, has been identified employing lawful software to illicitly access institutions in Taiwan.
This collective utilizes advanced methods, including those previously linked to another entity known as “Storm-0558,” to penetrate systems and siphon off confidential data.
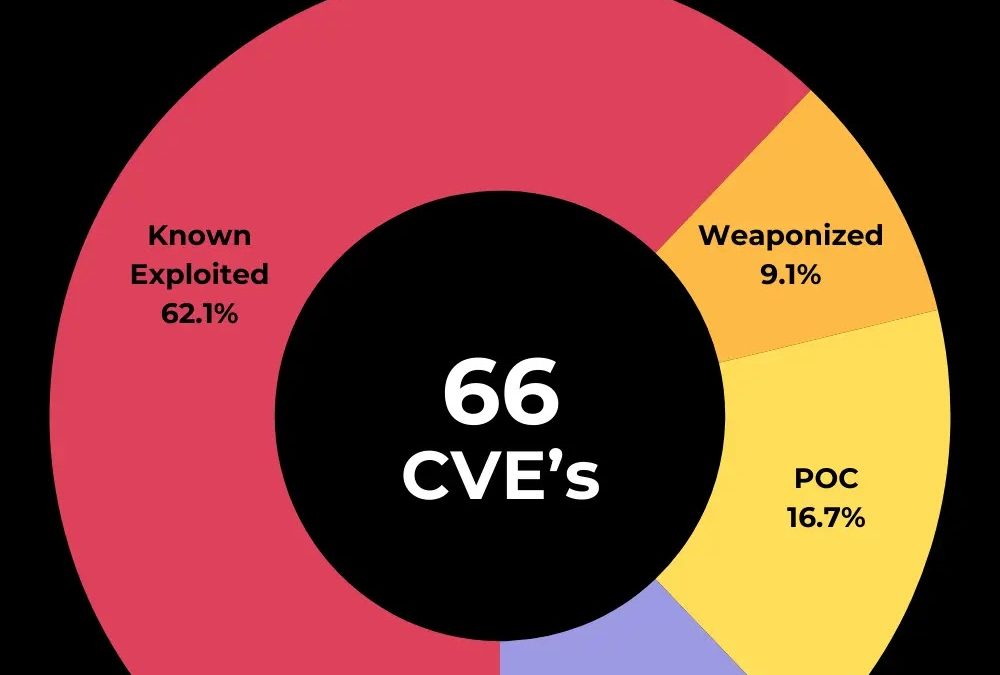
Recently, cybersecurity analysts at VulnCheck unearthed that the botnet belonging to Flax Typhoon has been actively taking advantage of 66 vulnerabilities across multiple devices.
Exploitation of 66 Vulnerabilities by Flax Typhoon’s Botnet
A collaborative Cybersecurity Advisory was issued by the intelligence organizations of Five Eyes (FBI, US Cyber Command, NSA, and partners from Australia, New Zealand, Canada, and UK) regarding a botnet affiliated with China dubbed Flax Typhoon.
This botnet exploits 66 distinct vulnerabilities (CVEs) in routers, IoT devices, and web-based applications.
Below, you will find a list of all the technologies targeted by the Flax Typhoon botnet, along with the number of vulnerabilities identified:
- Apache (10 CVEs)
- Cisco (5 CVEs)
- Zyxel (3 CVEs)
- QNAP (3 CVEs)
- Fortinet (3 CVEs)
- Draytek (3 CVEs)
- WordPress (2 CVEs)
- Telesquare (2 CVEs)
- Ivanti (2 CVEs)
- IBM (2 CVEs)
- F5 (2 CVEs)
- Contec (2 CVEs)
- Chamilo (2 CVEs)
The primary targets are the United States, with “47.9%” of affected devices, followed by Vietnam (8%) and Germany (7.2%).
The botnet has a global reach, impacting North America, Europe, and Asia. Out of the 66 vulnerabilities, the KEV database of VulnCheck initially listed ’41,’ while CISA’s KEV catalog had ’27.’
Subsequently, VulnCheck has released an updated version that includes all the 66 CVEs.
Prior to the advisory, “71.2%” of these vulnerabilities were already known to be exploited or weaponized, “16.7%” had proof-of-concept exploit code available, and “12.1%” lacked public evidence of exploitation.
This botnet operation poses a threat to critical infrastructure, especially in the United States, given the increased attention on the affected devices.
In addition, the advisory offers vital indicators of compromise and geographical data regarding impacted devices with the goal of enhancing awareness and fortifying cybersecurity defenses against this menace.
Actions to Alleviate the Threat
Listed below are all the proposed actions:
- Deactivate unused services and ports
- Establish network segmentation
- Monitor for unusually high network traffic
- Implement necessary patches and updates
- Substitute default passwords with robust alternatives
- Upgrade outdated equipment.
The article “Flax Typhoon’s Botnet Actively Exploiting 66 Vulnerabilities In Various Devices” was originally published on Cyber Security News.