“`html
Incident response Tools or incident management utilities are vital security measures to shield organizations and companies from cyber threats.
Our dependence on the internet is increasing, and thus do threats to businesses, despite enhanced funding and expertise in cyber protection. More data breaches and cyber incidents are affecting businesses, governments, and individuals than ever before.
Emerging technologies such as Machine Learning, Artificial Intelligence, and 5G, along with improved collaboration among hacker collectives and state entities, have intensified risks.
The quicker your organization identifies and reacts to unauthorized access or IoT security issues, the lesser the likelihood of detrimental effects on information, customer trust, reputation, and profitability.
What is an Incident Response?
Incident response denotes an organization’s methodology for addressing and managing a cyberattack.
A cyberattack or security breach may result in disorder, copyright disputes, a drain on overall organizational resources and time, and a reduction in brand worth.
The goal of incident response is to minimize damage and swiftly return to normality.
A well-articulated incident response strategy can limit the impact of an attack and conserve money and time post-cyber incident.
Incident response oversees the consequences of an IoT security breach or technical failure.
Having a response protocol established before an incident is crucial. This will lessen the damage caused and save the organization time and funds during the recovery phase.
Organizations frequently employ several premier incident response tools to discover and mitigate cyber threats.
Here we present some of the most significant cyber incident response software commonly utilized with advanced functionalities.
As you are aware, the investigation is always necessary to secure your future; you must familiarize yourself with and prepare for potential attacks.
Every organization should possess Security Incident Response technology capable of identifying and dealing with exploits, malware, cyberattacks, and other external security risks.
These Incident Response Tools typically collaborate with traditional security measures, such as firewalls and antivirus programs, to analyze threats before they occur.
To achieve this effectively, these tools collect data from logs, identity systems, endpoints, and more.
They also detect unusual behaviors within the system.
Utilizing these optimal Incident Response Tools makes it straightforward to monitor, resolve, and swiftly pinpoint security issues.
It simplifies the process and eliminates tedious manual tasks.
The majority of contemporary tools possess multiple capabilities to block and identify threats while also alerting security teams to investigate further issues.
Security terminology varies across different fields and is entirely contingent on the organization’s requirements.
In this context, choosing the right tool can be quite challenging and must align with your specific needs.
What’s in the Incident Response Tools Article?
- Introduction
- Why Incident Response software is Essential?
- What is an Incident Response?
- Incident Response Stages
- What is an Incident Response Tool?
- Why do we utilize Incident Response Tools?
- Table of Contents
- Incident Response Tools Features
- Demo Video
- Pros & Cons
- IR Tool Users
- Costs for each Tool
- Conclusion
Incident Response Stages
The incident response methodology consists of six key steps: preparation, identification, containment, eradication, recovery, and lessons learned.
| Incident Response Phases | How to React |
| Preparation | This involves identifying the exact members of the response team and the triggers for internal partner alerts. |
| Identification | This is the procedure for detecting threats and responding quickly and effectively. |
| Containment | After determining the course of action, the next step is to limit the damage and prevent it from escalating. |
| Eradication | This step involves removing the threat and restoring internal systems as accurately as possible to their original state. |
| Recovery | Security professionals must verify that all compromised systems are no longer vulnerable and can be safely brought back online. |
| Lessons Learned | One of the most vital yet often overlooked stages. The incident response team and its partners convene to discuss improvements for future responses. |
In today’s technology-driven world, organizations encounter escalating security threats that are becoming unavoidable.
Thus, the incident response team requires effective incident response tools to overcome and manage security challenges.
Let’s first explore what an incident response tool is and delve deeper into the tools.

Although companies have numerous security measures in place, the human element remains the most critical.
According to the annual Verizon Data Breach Investigations
“““html
Reports indicate that phishing attempts account for over 85% of all security breaches.
IT security experts must be prepared for the worst, as 13% of breaches caused by individuals involve ransomware, with 10% of these ransomware incidents costing companies an average of $1 million.
Consequently, organizations ought to allocate resources toward incident response software.
The incident response tools are vital, as they assist enterprises in identifying and addressing cyberattacks, manipulation, malware, and various security threatsboth internally and externally within a reasonable timeframe.
Modern incident response software typically encompasses several features, including automatic detection and blocking of threats while alerting relevant security teams to examine the situation.
Incident response tools can be utilized in numerous ways depending on the specific requirements of the organization.
This may include overseeing the system and individual nodes, networks, assets, users, and more.
Numerous organizations struggle to select the most suitable incident response software.
To assist you in finding an appropriate solution, here is a compilation of incident response tools designed to help you identify, deter, and manage various security threats and assaults on your IoT security systems.
We assessed the industry focusing on safeguarding digital assets and consulted subject matter experts regarding the particular needs of their sectors based on the following criteria.
How efficiently do the incident response software perform in the following activities?
- Preparation & Identification
- Containment & Eradication
- Recovery and Restoration
- False Positive Event Checks
- Incident Identification
- Containment and Quarantine of attackers and incident activities
- Recovery from incidents, including system restoration
- Features, Speed, User-Friendliness
- Activities in every phase of incident response
Incident Response Market
| Incident Response Tools | Key Features |
|---|---|
| 1. ManageEngine Log360 | 1. It analyzes on-site systems and cloud environments. 2. Logs are aggregated and retained. 3. Employs User and Entity Behavior Analytics (UEBA) to monitor standard events. 4. The ManageEngine suite includes additional security functionalities like data integrity monitoring and a threat intelligence 5. feed to expedite threat hunting. |
| 2. SolarWinds | 1. User Activity Surveillance. 2. File Integrity Oversight. 3. Network Security Surveillance. 4. Analysis of Microsoft IIS Logs. 5. Management of Firewall Security. 6. Network Security Instruments. 7. Snort IDS Log Analysis. |
| 3. CrowdStrike Falcon Insight XDR | 1. Exceptional coverage 2. Accelerated investigations 3. Integration of threat intelligence 4. Round-the-clock managed threat hunting 5. Continuous capture of raw events 6. Proactive threat exploration |
| 4. IBM QRadar | 1. Outstanding filtering to achieve desired results 2. Excellent capabilities for threat identification 3. Netflow examination 4. Rapid analysis of substantial data sets 5. Detection of concealed threats 6. User behavior analytics |
| 5. Splunk | 1. Identifying network complications and ensuring security and scalability is straightforward. 2. It also aids in tracking logs and databases. 3. It features an intuitive and informative web interface that facilitates network monitoring. |
| 6. AlienVault | 1. Compatible with both Linux and Windows 2. Behavior monitoring 3. Intrusion detection 4. Log analysis and management 5. Ability to manage compliance |
| 7. LogRhythm | 1. It includes a response playbook 2. Automated intelligent responses 3. Open-source backend for Elasticsearch. 4. Enhanced integration of threat data 5. Assessing file integrity |
| 8. Varonis | 1. Investigating potential incidents 2. Containment, eradication, and recovery 3. Guidance on detection, processes, and cyber resilience 4. In-depth forensic analysis |
| 9. OpenVAS | 1. An Advanced Task Wizard is integrated into the OpenVAS web interface. 2. It offers various default scan settings and allows users to customize configurations. 3. Reporting and suggestions for problem resolution 4. Incorporating security tools with others |
| 10. Rapid7 InsightlDR | 1. Endpoint Detection and Response (EDR) 2. Network Traffic Analysis (NTA) 3. User and Entity Behavior Analytics (UEBA) 4. Cloud and Integration capabilities. 5. Security Information and Event Management (SIEM) 6. Integrated Threat Intelligence. 7. MITRE ATT&CK Alignment. 8. Deception Technology. |
| 11. Snort | 1. Modifications and expansions are possible. 2. Custom tests and plugins are supported “““html 3. Open-source and adaptable 4. passive and inline |
| 12. Suricata | 1. It generates JSON output 2. It accommodates Lua scripting 3. Support for pcap (packet capture) 4. This tool allows multiple integrations. |
| 13. Nagios | 1. It is easy to detect network problems and ensure security and scalability. 2. It also assists in monitoring logs and databases. 3. It features a user-friendly and informative web interface that simplifies network observation. |
| 14. Sumo Logic | 1. Monitor & troubleshoot 2. Incorporate real-time threat intelligence 3. Monitor & troubleshoot 4. aggregated logs, metrics, and traces 5. Rapidly identify applications & incidents |
| 15. Dynatrace | 1. Comprehensive stack availability and performance monitoring 2. Straightforward monitoring without configuration 3. Automated Incident Management 4. AWS Monitoring 5. Azure Monitoring 6. Kubernetes Monitoring |
- ManageEngine – Delivers all-encompassing IT management software focusing on network and device oversight.
- SolarWinds – Provides robust and user-friendly network management software utilized for system and network monitoring.
- CrowdStrike Falcon Insight XDR – Endpoint detection and response (EDR) tool offering sophisticated threat detection, investigation, and proactive measures.
- IBM QRadar – Security information and event management (SIEM) platform that consolidates log data and network flows for threat identification.
- Splunk – Software platform for exploring, analyzing, and visualizing machine-generated data collected from applications, websites, sensors, devices, etc.
- AlienVault – (now AT&T Cybersecurity) Delivers SIEM and threat intelligence functionalities, merging various security capabilities into a unified platform.
- LogRhythm – NextGen SIEM platform that merges advanced analytics with user and entity behavior analytics (UEBA), network detection, and response capabilities.
- Varonis – Data security platform that safeguards sensitive data against insider threats, streamlines compliance, and guarantees privacy.
- OpenVAS – Open-source vulnerability scanning solution that evaluates computers for recognized vulnerabilities.
- Rapid7 InsightIDR – Cloud-native SIEM solution providing detection, investigation, and responses to mitigate risk and address security incidents.
- Snort – Open-source network intrusion prevention system (NIPS) and detection system (NIDS) conducting packet logging and real-time traffic analysis.
- Suricata – Open-source network threat detection engine capable of real-time intrusion detection (IDS), intrusion prevention (IPS), and network security monitoring (NSM).
- Nagios – Open-source software for overseeing systems, networks, and infrastructure, providing notifications for failures and recoveries.
- Sumo Logic – Cloud-based log management and analytics service that utilizes machine-generated data for instant IT insights.
- Dynatrace – Software intelligence platform that offers automated cloud operations and real-time analytics for modern and dynamic environments.

The ManageEngine Security Incident Response Tool streamlines threat detection, evaluation, and response to security incidents. It collects security alerts from the IT ecosystem, implements defined workflows for incident assessment and prioritization, and provides monitoring dashboards.
The platform enhances collaboration among IT teams, automates routine tasks, and generates comprehensive reports on incident management efficiency and compliance, improving an organization’s security issue response time.
Features
- Automated Active Directory management, delegation, and extensive user administration.
- A single endpoint for patch management, software deployment, remote access, and mobile device oversight.
- A network monitoring solution enables the observation of speed, faults, and real-time activities.
- Application performance monitoring across various systems and infrastructures.
- Cloud monitoring encompasses websites, servers, applications, and network devices.
| What is good? | What could be refined? |
|---|---|
| Customizable tools | Self-service capabilities and knowledge bases for users require enhancement. |
| Highly valuable interface | Modifying settings while mobile is complex. Thus, the interface and user experience need improvement. |
| Very effective ticketing system | Issues with the interface reported |

The SolarWinds Security Incident Response Tool swiftly identifies and resolves cybersecurity challenges. Its integration with SolarWinds’ network management suite automates responses to security alerts.
The solution ranks incidents by seriousness, provides customizable playbooks for uniform response strategies, and facilitates real-time collaboration among security teams. Additionally, it features comprehensive logging and reporting for post-incident evaluations and compliance reviews.
Features
- It accommodates various devices and brands, simplifying network installations.
- SolarWinds sends alerts and reports according to your restrictions and criteria—resolving issues proactively.
- Both small and large organizations can enhance monitoring capabilities as their networks evolve due to its adaptability.
- The SolarWinds interface is straightforward, with dashboards displaying essential network information.
| What is good? |
|---|
“““html

CrowdStrike Falcon Insight XDR delivers endpoint detection and response (EDR) security. It identifies and reacts to dangers across endpoints, cloud resources, and networks utilizing AI and behavioral analysis.
The platform provides immediate visibility, automated threat reconnaissance, and response capabilities. It integrates with the security ecosystem to streamline incident management and assist organizations in countering intricate security challenges.
Attributes
- Falcon Insight XDR’s advanced EDR functionalities recognize and neutralize threats across all endpoints in real-time.
- Protection and monitoring are extended to Windows, macOS, Linux, and additional operating systems and devices.
- Behavioral analysis and machine learning identify and thwart device threats and dubious activities.
- Integrating threat intelligence data aids in identifying and countering both new and existing threats.
- Facilitates prompt security interventions, including containment, isolation, and remediation.
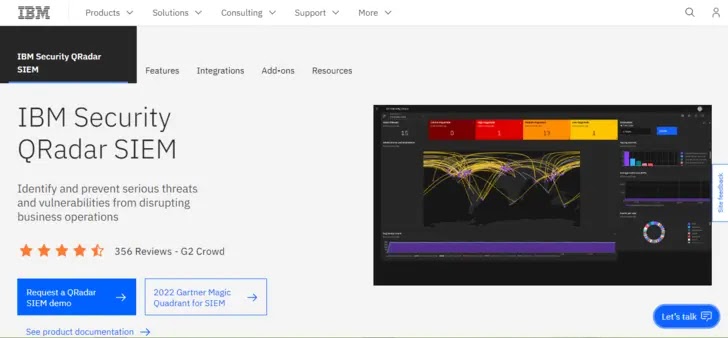
IBM QRadar is a comprehensive SIEM solution that utilizes log and event data across a network to pinpoint security concerns. It identifies anomalies and breaches through robust analytics, enabling swift incident response.
QRadar streamlines data collection and activity correlation, offering real-time alerts, dashboards, and detailed reporting to enhance security operations and compliance management.
Attributes
- Analyzes log data from multiple sources for security threats and abnormal activities.
- Aids SIEM in identifying risks by correlating network events.
- Real-time monitoring and automated responses support incident management.
- Aggregated threat data sources simplify the identification of known and emerging threats.
| What is advantageous? | What could be enhanced? |
|---|---|
| Thorough Integration | The initial setup and configuration can be intricate |
| It is highly adaptable | Steep Learning Curve |
| Provides real-time oversight |

To accelerate incident management, Splunk SOAR (formerly Phantom) automates and organizes tasks across security systems. It centralizes security event management, allowing teams to implement predefined action plans for various scenarios.
Splunk SOAR connects with existing security infrastructure, automates tasks through playbooks, and supplies real-time analytics to enhance decision-making and reduce manual intervention, thus bolstering security through coordinated responses.
Attributes
- Collects and indexes logs, metrics, and machine-generated data.
- Enables real-time searching and analysis of extensive datasets.
- Examines data from various sources and produces dashboards for clarity.
- Employs machine learning and AI to detect patterns, anomalies, and forecasts.
- Log analysis and monitoring assist with security, threat detection, and compliance.
| What is advantageous? | What could be enhanced? |
|---|---|
| It includes numerous extensions and add-ons | The cost for data is generally elevated for larger datasets. |
| It provides an impressive dashboard with visualization and search functionalities. | Ongoing attempts to replace it with open-source alternative software |
| It produces analytical reports utilizing visual graphs and communal tables and charts. |

AlienVault Security Incident Response Tool merges threat identification, incident management, and compliance oversight. It automates security functions with immediate alerts, forensic assessment, and remediation.
Continuous surveillance and a threat intelligence repository reveal vulnerabilities and attacks, expediting response. It assists security teams in handling and alleviating security challenges in diverse IT environments.
Attributes
- It combines asset discovery, vulnerability evaluation, threat identification, and incident management.
- Provides infrastructure visibility by automatically recognizing and cataloging network assets.
- Conducts continuous scans to identify and prioritize vulnerabilities to mitigate risk.
- Automates workflows and offers actionable insights to resolve incidents promptly.
| What is advantageous? | What could be enhanced? |
|---|---|
| It boasts a consolidated security platform | If the systems utilized by cross-border collaborators are unreliable, it might be relatively easy to initiate attacks against their databases. |
| Endless threat intelligence | This may impair the system’s capacity to identify threats. |
| Diverse deployment alternatives |

LogRhythm’s Security Incident Response Tool is crafted for effective cybersecurity threat identification and reaction. It merges with the current security infrastructure to automate processes, allowing quick recognition and alleviation of threats.
This tool offers real-time oversight, expansive reporting, and intelligent response capabilities, promoting efficient incident management and ensuring adherence to regulatory standards.
Features
- Facilitates SIEM log collection, correlation, and examination.
- Logs from various origins are compiled and normalized for centralized threat detection.
- Recognizes anomalies and security threats employing behavioral analysis and machine learning.
- Aids in averting security incidents with instantaneous threat identification and response.
- Enhances incident resolution by automating processes.
| What is good? | What could be better? |
|---|---|
| Log ingestion | Diverse equipment with unique entry points |
| Utilizing the AI engine’s guidelines, it swiftly identifies confrontational activities. | Performing extensive web searches during traffic can render it somewhat unstable. |
| Integrates SIEM, UEBA, and SOAR functionalities. |
Varonis Security Incident Response Tool automates the discovery and reaction to security threats in data-focused environments. It evaluates user behavior and data access trends, utilizing machine learning to pinpoint anomalies suggestive of breaches or insider risks.
This tool delivers real-time alerts, simplifies investigations, and provides actionable insights, boosting an organization’s capability to promptly address incidents and mitigate risks.
Features
- Offers visibility, classification, and management for sensitive structured and unstructured data.
- Behavioral analytics identify and prevent insider threats and unusual data access.
- Tracks user behavior for security threats and unauthorized access.
- Restricts access, encrypts data, and monitors it to categorize and secure sensitive data.
- Delivers thorough audit and compliance reports.
| What is good? | What could be better? |
|---|---|
| Assists in data security, access, and sensitive data management. | Complicated Integration |
| Data discovery & classification | Requires continuous monitoring and upkeep for optimal operation. |
| Insider Risk Management Software |

OpenVAS (Open Vulnerability Assessment Scanner) is an all-inclusive security tool for uncovering vulnerabilities in network services and systems.
It automates scanning and analysis to reveal security weaknesses, utilizing a frequently updated database of known vulnerabilities. The tool provides detailed reporting to assist in incident response, enabling organizations to prioritize and address security threats efficiently.
Features
- Thoroughly inspects networks and systems for security gaps.
- Identifies and maps network assets to depict the entire system.
- Regularly updates vulnerability tests to tackle new threats and weaknesses.
- Web application scanning and security flaw detection are available.
- Evaluates system setup for weaknesses and errors that may be exploited.
| What is good? | What could be better? |
|---|---|
| Frequent vulnerability check updates and community support. | Installation, configuration, and usage can be challenging |
| Enables scan policy customization. | Potential false positives necessitate manual verification. |
| Supports multiple operating systems. |

The Rapid7 Security Incident Response Tool automates the coordination, investigation, and response to security incidents. It is integrated with existing security systems to collect and analyze data, furnishing real-time insights and actionable intelligence.
This tool prioritizes threats based on severity, optimizes workflows for efficiency, and ensures compliance with reporting requirements, enhancing an organization’s capacity to swiftly and effectively mitigate security risks.
Features
- Includes advanced SIEM tools for collecting, analyzing, and linking logs.
- User activity analytics (UBA) identifies unusual user actions and insider threats through behavioral analysis.
- This functionality facilitates monitoring endpoints and thwarting threats.
- Compiles and normalizes log data from numerous sources for centralized analysis and threat detection.
- This feature displays current network security threats and odd behavior.
| What is good? | What could be better? |
|---|---|
| Endpoint Detection and Response (EDR) | Subscription data is limited |
| Cloud and Integrations | Yearly plan is pricier than other providers |
| MITRE ATT&CK Alignment | Prices vary for local and international |
“““html

Snort is a free, open-source system for detecting network intrusions (NIDS) that conducts real-time analysis of traffic and logs packets. It employs rule-based logic to pinpoint malicious actions, such as attacks or scans, by scrutinizing packet headers and payloads.
Snort notifies administrators about potential threats through its logging features, enabling prompt incident response and improving network security.
Features
- Examines real-time network data for irregularities and hazards.
- Detects attack signatures and other unwanted activities using established patterns.
- Monitors network protocols for atypical or illicit actions.
- Ineates alerts when rules and signatures correspond.
- Administrators can formulate and personalize detection regulations for network security.
| What is good? | What could be better? |
|---|---|
| It installs swiftly and effortlessly on networks. | The administrator must devise their own methods for logging and reporting. |
| Writing rules is straightforward. | Token ring connections are unsupported in Snort. |
| It boasts substantial support available on Snort websites and its dedicated mailing list. | |
| It’s free for administrators seeking a budget-friendly IDS. |

Suricata is a free, open-source network security solution that serves as an intrusion detection system (IDS), an intrusion prevention system (IPS), and a network security monitoring (NSM) tool.
It analyzes network traffic leveraging a rule-based language to identify and prevent malicious activities. Suricata is multi-threaded, adept at managing high throughput, and supports real-time analysis and logging.
Features
- Multi-threading enhances traffic speed and overall performance.
- Signatures and rules ascertain network threats and attack patterns.
- Real-time standards evaluation checks for unusual behaviors and security anomallies.
- Examines network data for irregularities.
- Investigates network data files for threats or abnormal activities.
| What is good? | What could be better? |
|---|---|
| High performance and scalability. | Configuration can be complicated. |
| Effectively handles network traffic through multi-threading. | There is a significant learning curve. |
| Supports automatic protocol recognition. |
Nagios Security Incident Response Tool enables real-time oversight and alerts for IT infrastructure security challenges. It identifies unauthorized access, system inconsistencies, and configuration adjustments, promoting swift incident responses.
This tool integrates with current security frameworks, offers customizable alert features, and aids compliance by continuously monitoring and logging security events.
Features
- Provides real-time monitoring of IT servers, applications, services, and networks.
- Generates configurable email, SMS, and other alerts for critical matters.
- Distributed monitoring accommodates both small and extensive environments.
- Utilizes performance graphs and reports to evaluate historical data and trends.
- Its adaptable plugin framework permits users to incorporate tracking checks and modify the software.
| What is good? | What could be better? |
|---|---|
| Extensive monitoring capabilities across various servers. | Network throughput, bandwidth, and availability issues cannot be monitored. |
| Usability for customization and extensibility. | The free version includes limited features. |

Sumo Logic’s Security Incident Response Tool utilizes analytics and cloud-based log management to identify, examine, and react to cybersecurity threats. It aggregates data from multiple sources, delivering real-time visibility and automated threat detection.
This enables rapid incident response by correlating and analyzing security data, helping organizations effectively mitigate risks and maintain compliance.
Features
- Provides cloud-centric log management and analytics for real-time machine data insights.
- Collects and organizes logs and data from diverse systems.
- Offers advanced analytics and visualization tools to uncover data trends and insights.
- Delivers log examination for security, threat detection, and compliance.
- Identifies trends and anomalies, forecasting future occurrences using machine learning.
| What is good? | What could be better? |
|---|---|
| Cloud-native SaaS analytics. | Excessive options complicate integration. |
| Top-tier infrastructure monitoring. | Can be expensive for substantial data volumes. |
| Numerous native integrations. |

Dynatrace Security Incident Response Tool merges with its APM solution to deliver real-time threat detection and automated responses. It utilizes AI to assess dependencies and configurations, identifying vulnerabilities and suspicious actions.
The tool enhances incident management by automating alerts and responses, improving security posture via continuous monitoring, and integrating smoothly with existing security processes.
Features
- Monitors all applications, services, infrastructure, and user experiences across the entire stack.
- AI-driven cause-and-effect analysis identifies performance issues in real-time.
- Offers recommendations for performance enhancement based on AI insights.
- Oversees cloud-native and hybrid environments, granting complete infrastructure control.
| What is good? | What Could Be? |
|---|---|
| User-friendly infographics. | Limited interactivity. |
| Explores process-to-process relationships. | The price can be somewhat high. |
“`

