“`html
Remote surveillance and management (RMM) instruments are essential for IT squads, but that same efficiency renders them a favored tactic for attackers as well.
During the initial half of 2025, ANY.RUN investigators examined numerous real-world malware activations within an interactive sandbox and identified a distinct pattern: five tools were frequently involved in the majority of RMM-related breaches.
Let’s delve deeper into the five RMM tools predominantly misused by attackers and how your team can detect this behavior more swiftly, before it escalates into a more significant issue.
If you are employed in a SOC or manage incident response, this is the type of trend deserving attention.
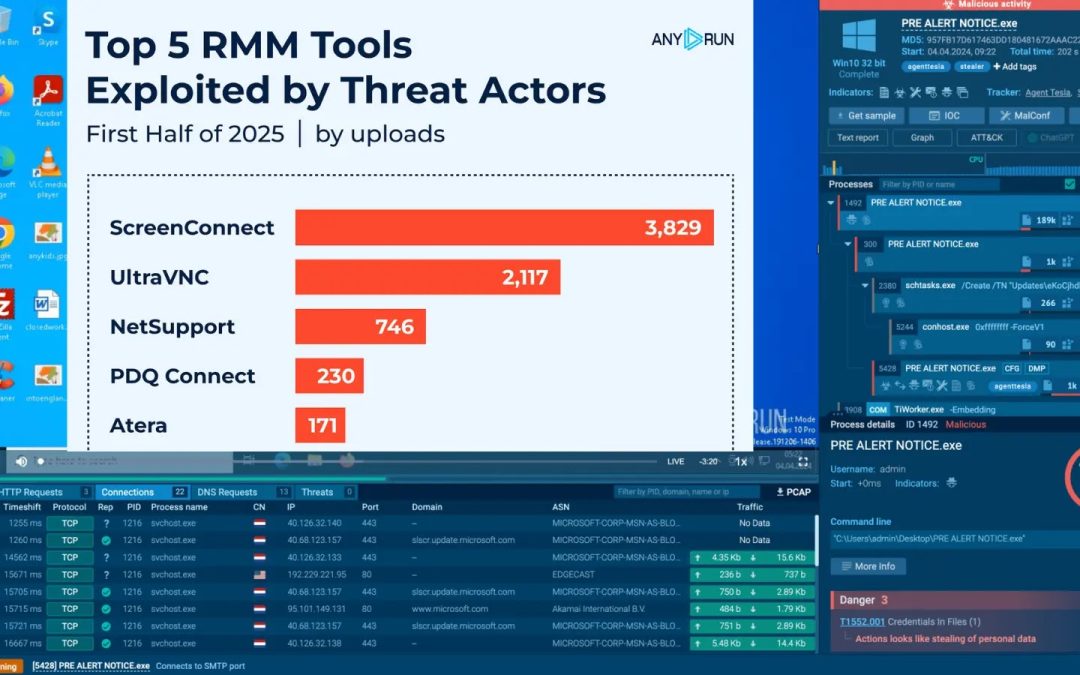
Overview of the Data
.webp)
This analysis showcases the occurrence rate of each RMM tool detected across dubious and harmful sandbox sessions in the first half of 2025.
The statistics are derived from ANY.RUN’s internal tagging system, which observes tool usage tendencies in real time.
It offers a rapid glance to identify which platforms were prominent in attacker movements and how often they surfaced in actual malware inquiries.
1. ScreenConnect: 3,829 Sandbox Sessions
ScreenConnect (now marketed as ConnectWise Control) is a legitimate remote assistance and desktop access utility utilized by IT teams and MSPs.
Regrettably, its robust remote control capabilities also render it a tempting option for malicious entities seeking discreet access and management of compromised systems.
In the subsequent sandbox session, we can distinctly observe how ScreenConnect is exploited in a phishing attempt that imitates a Zoom meeting link:

The quickest method to identify threats like this is through interactive sandboxes like ANY.RUN.
In the upper-right section of the session, the platform promptly labels the activity as Malicious, assigning explicit behavioral tags such as “screenconnect”, “rmm-tool”, and “remote”.

The process tree points out the harmful executable (ScreenConnect.WindowsClient.exe) and offers comprehensive context such as the command line, YARA detections, and more, eliminating your time and guesswork.
Instead of sifting through logs or depending on static detection, this real-time visibility enables teams to identify abuse early, even when attackers employ legitimate tools.

2. UltraVNC: 2,117 Sandbox Sessions
UltraVNC is an open-source remote desktop application frequently utilized by IT support teams to observe and manage another computer over a network. It’s lightweight, free, and simple to configure.
In the sandbox session below, UltraVNC is employed as part of an Agent Tesla operation.
.webp)
ANY.RUN’s interactive sandbox immediately flags the behavior, designating the session as Malicious and tagging it with “ultravnc”, “rmm-tool”, and “stealer”.
The process tree illustrates how RegAsm.exe initiates with dubious behavior and connects to Agent Tesla activity, including credential larceny.
With real-time detection, precise indicators, and visualized execution flow, ANY.RUN assists analysts in swiftly connecting the dots, without needing to reverse engineer every step manually.
3. NetSupport: 746 Sandbox Sessions
NetSupport…
“““html
Manager is a valid remote access application frequently utilized in corporate and educational environments. However, when activated from unexpected locations and without user approval, it raises concerns.
Malicious actors often employ it as a covert Remote Access Trojan (RAT) due to its integrated functions for screen observation, file transmission, and command enactment.
In the sandbox instance below, the assault initiates with a text file harboring obscured PowerShell commands, which activates client32.exe; a NetSupport binary placed into the user’s roaming profile:

The process hierarchy reveals client32.exe executing from:
C:UsersadminAppDataRoamingbDabSkclient32.exe. This is a common directory employed by malware to elude detection. 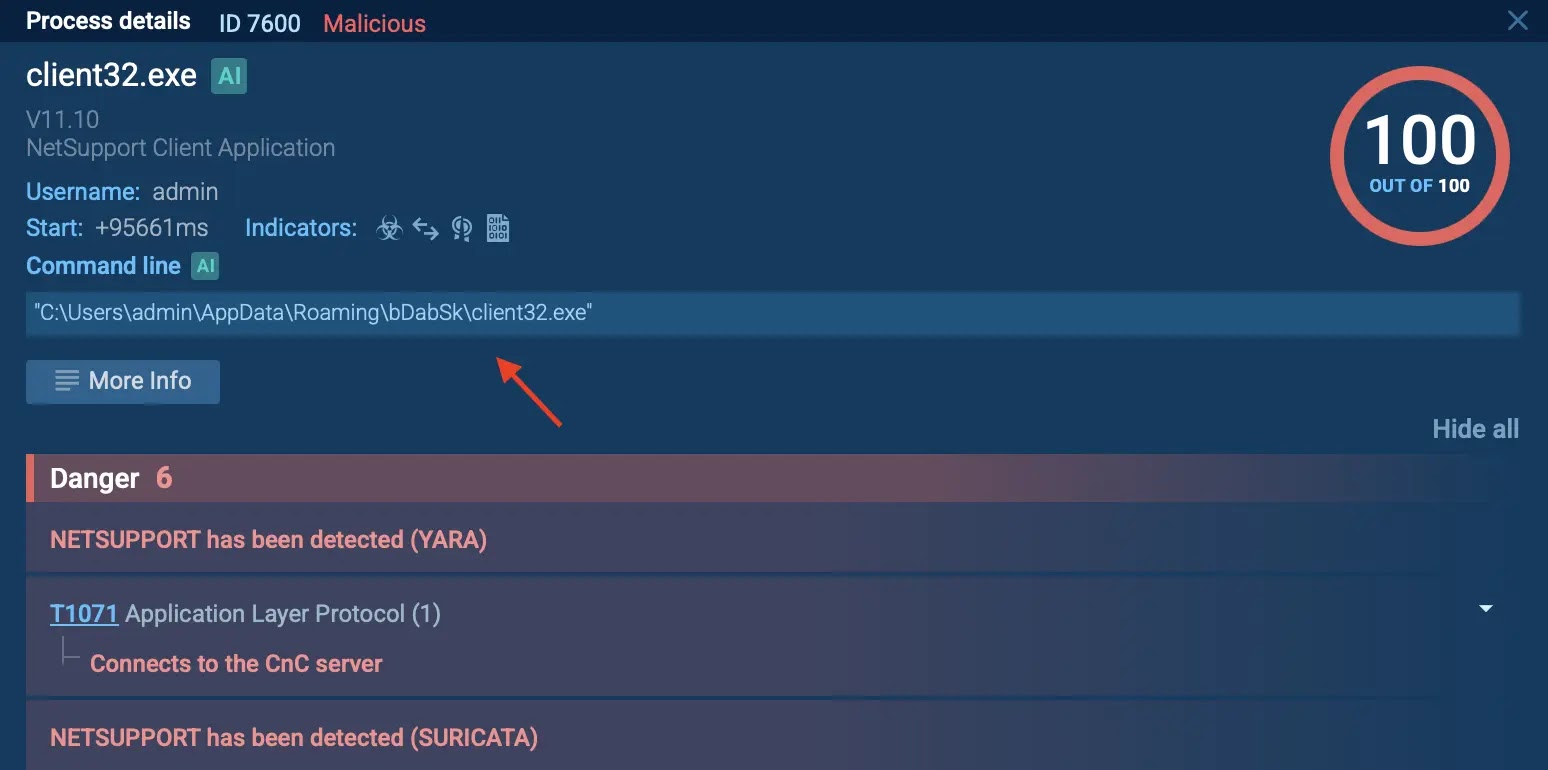
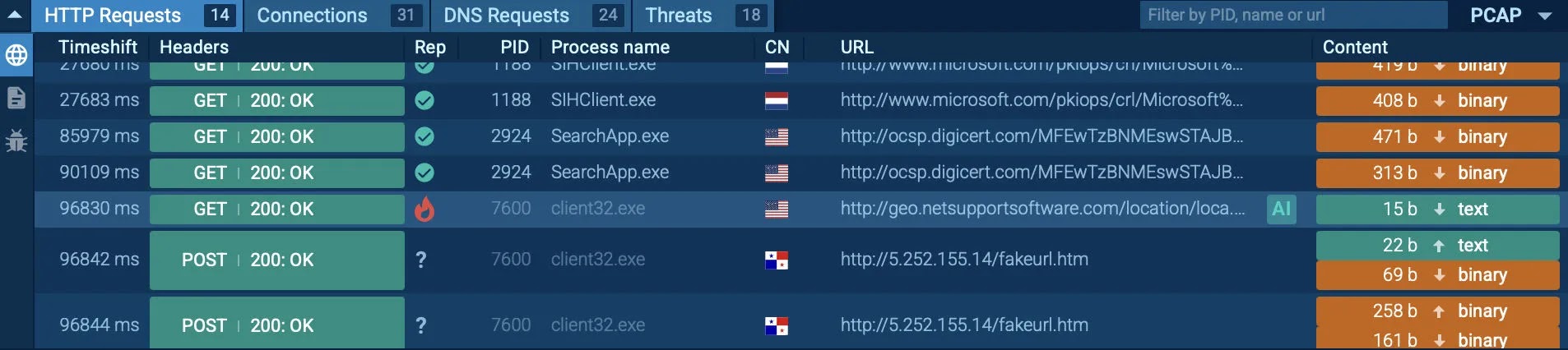
Below, in the HTTP request segment, we observe a link to the dubious domain geo.netsupportsoftware.com, affirming the utilization of NetSupport for command-and-control.
Coupled with POST traffic to a fraudulent C2 server, this activity aids analysts in rapidly and confidently connecting the dots.
.webp)
4. PDQ Connect: 230 Sandbox Sessions
PDQ Connect is a cloud-centered system administration solution that permits IT teams to install software, execute scripts, and manage endpoints remotely, without requiring domain access.
It is often exploited in phishing and initial access schemes.
In the sandbox instance beneath, the attack commences with a fraudulent government verification page; a phishing site designed to entice the target into downloading a harmful payload:
.webp)
Shortly after the phishing page appears, we notice a questionable connection from pdq-connect-agent.exe to a remote IP address (162.159.141.50) over port 443, as depicted in the network flow.
The executable shows up alongside a companion updater process, pdq-connect-updater.exe, indicating a covert installation and command channel.
.webp)
This configuration can effortlessly escape detection in static or rule-based systems.
However, ANY.RUN’s interactive sandbox exposes it in seconds, pinpointing the precise process generating the outbound request and furnishing analysts with a comprehensive view of what transpired, from the fake CAPTCHA to the real-time network activity.
5. Atera: 171 Sandbox Sessions
Atera is a remote monitoring and management (RMM) platform crafted for IT specialists to oversee systems remotely, automate maintenance, and track performance.
Similar to other legitimate tools, it can be discreetly installed and misappropriated by attackers for persistence and control, often without triggering alerts.
In the sandbox session below, the file AteraAgent.exe operates from its standard directory yet triggers several warnings associated with system service execution, file replacements, and suspicious process activities:
ANY.RUN’s detection mechanism categorizes this as Malicious.
The process drops or overwrites executable files and initiates SC.EXE to register itself as a Windows service; typical behavior in obscure persistence configurations.
.webp)
In the Threat Details tab, we also observe an outbound connection to agent-api.atera.com, marked as a Potential Corporate Privacy Violation.
This detection (via Suricata IDS) verifies that the Atera agent is actively communicating with remote infrastructure, regardless of user awareness.
.webp)
With this level of insight, teams can swiftly identify when a trusted utility crosses into unauthorized usage and take measures before more extensive breaches occur.
Identify Misuse Early And Act With Assurance
RMM tools are not disappearing, but with the appropriate visibility, your team doesn’t have to be caught unprepared when they’re weaponized against you.
ANY.RUN aids security teams in detecting misuse promptly, investigating intelligently, and making improved decisions with context-rich, real-time assessments.
From immediate verdicts and comprehensive behavioral tags to network forensics and attack mapping, ANY.RUN provides analysts with the tools they require to stay ahead, without sifting through logs or solely relying on static detections.
Whether you’re operating in a SOC, conducting threat hunts, or probing incidents, it is designed for speed, clarity, collaboration, and reliability.
“`