There has been a critical security flaw identified in various Xerox printer models, enabling individuals with administrative privileges to gain full control over the devices.
SEC Consult has reported a significant vulnerability, recognized as CVE-2024-6333, impacting multiple printer series such as EC80xx, AltaLink, VersaLink, and WorkCentre.
This security loophole grants authenticated attackers the ability to execute unauthorized commands with root access on the printer’s OS through the web interface.
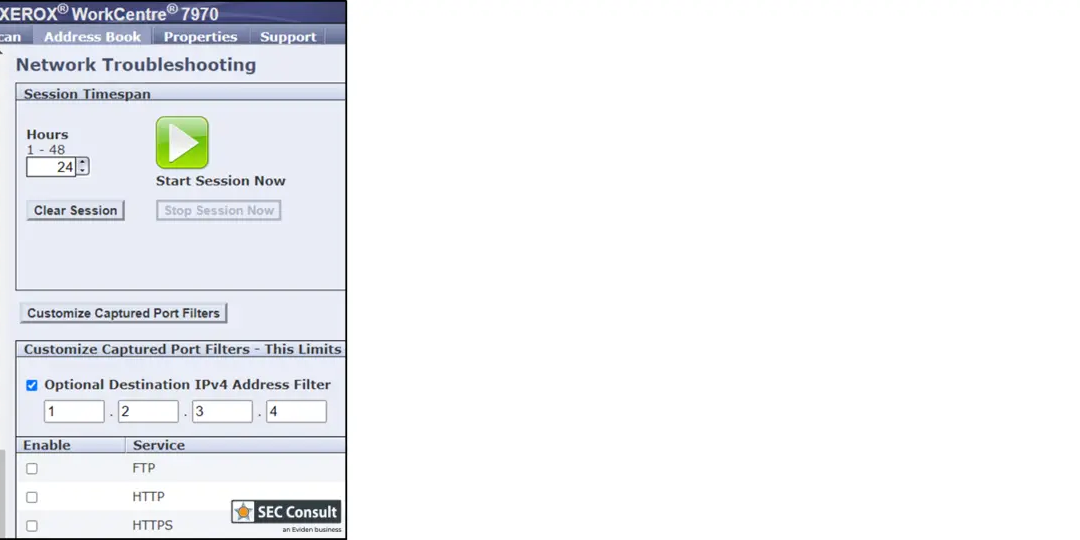
Within the “Network Troubleshooting” option, an RCE vulnerability exists, allowing system administrators to configure network troubleshooting settings using the tcpdump utility.
This vulnerability originates from inadequate validation of input in the IPv4 address field of the network troubleshooting function.
By inserting malicious OS commands into the tcpdump command line, attackers can compromise the entire system.
By combining this with previously patched vulnerabilities, attackers may establish continuous access to impacted devices.
With a severity rating of 7.2 (HIGH) on the CVSS scale, affected devices include:
- AltaLink B8045/B8055/B8065/B8075/B8090 series
- AltaLink C8030/C8035/C8045/C8055/C8070 series
- Various VersaLink and WorkCentre models
Steps for Mitigation
Security specialists strongly advise organizations to take prompt action by:
- Implementing the most recent security patches outlined in Xerox Security Bulletin XRX24-015.
- Ensuring all prior security updates are installed, including those specified in bulletin XRX23-020.
- Conducting comprehensive security evaluations of their printer setup.
The Vulnerability Lab at SEC Consult discovered this issue, underlining the necessity of adequate security measures for network-connected printing devices.
Businesses utilizing impacted Xerox printers should prioritize these updates to safeguard their infrastructure against potential breaches.
The article originally appeared on Cyber Security News