“`html
A complex new variant of the macOS.ZuRu malware has arisen, aiming at macOS users via a compromised iteration of the widely-used Termius SSH client.
This new version, uncovered in late May 2025, signifies a significant advancement in the tactics of threat actors, shifting from their typical Baidu search engine poisoning schemes to directly infiltrate genuine applications utilized by developers and IT specialists.
The ZuRu malware family was first detected in July 2021 when a Chinese blogger revealed trojanized versions of renowned macOS utilities being disseminated through tainted search results.
Initially aimed at applications such as iTerm2, SecureCRT, and Microsoft Remote Desktop, the malware has consistently targeted tools frequently employed by backend developers and system administrators requiring SSH and remote connectivity features.
SentinelOne analysts detected this new variant as part of their continuous surveillance of macOS threats, highlighting substantial technical enhancements in the malware’s execution methods.
The threat actors have abandoned their earlier dynamic library injection strategy in favor of a more advanced method that embeds harmful components directly within the target application’s helper processes.
%20and%20the%20trojan%20(bottom)%20with%20two%20extra%20binaries%20(Source%20-%20SentinelOne).webp)
The compromised Termius application appears as a disk image file of 248MB, significantly larger than the original 225MB version due to the incorporated malicious binaries.
The attackers have substituted the initial developer signature with their own makeshift signature to bypass macOS code signing regulations, showcasing their comprehension of Apple’s security frameworks.
This progression signals a troubling trend toward more direct application infiltration, potentially evading conventional detection strategies that concentrate on external library injection.
The ongoing effectiveness of the malware indicates that environments lacking strong endpoint defense remain susceptible to these advanced social engineering schemes.
Infection Mechanism and Persistence Tactics
The malware utilizes a multi-phase infection strategy that commences with the alteration of the authentic Termius Helper.app component.
The original 248KB Termius Helper binary is renamed to .Termius Helper1, while a hefty 25MB harmful substitute occupies its position.
Upon execution, this trojanized helper activates both the original application to ensure typical functionality and the malware loader .localized to commence the infection sequence.
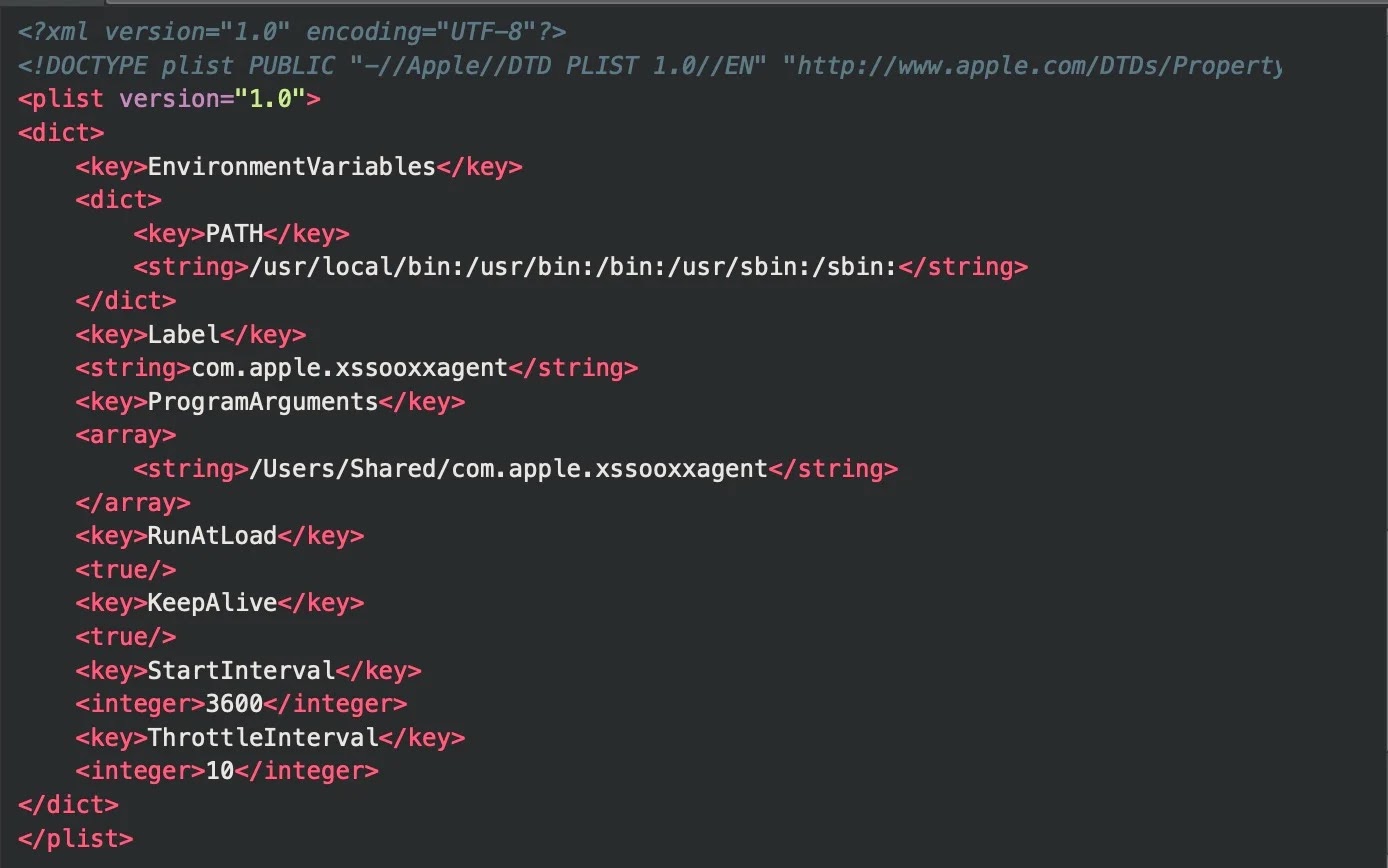.webp)
The loader secures persistence by generating a LaunchDaemon with the label com.apple.xssooxxagent, programmed to execute every hour from /Users/Shared/com.apple.xssooxxagent.
It retrieves an encrypted payload from download.termius[.]info/bn.log.enc utilizing the hardcoded decryption key my_secret_key, writing the decrypted Khepri C2 beacon to /tmp/.fseventsd.
The beacon maintains a fast 5-second heartbeat with the command and control server at ctl01.termius[.]fun, employing port 53 to merge with legitimate DNS traffic while utilizing www.baidu[.]com as a decoy domain.
“`

