Cyber Security
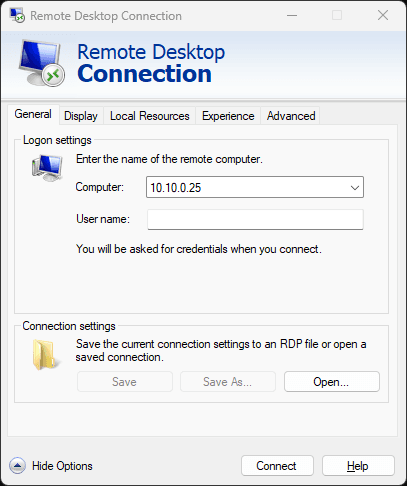
Microsoft’s Remote Desktop Protocol (RDP) has unveiled an obscure yet pivotal security attribute informally termed as “incognito mode” utilizing its /public command-line parameter. This feature, officially labeled as public mode, bars the client from...

Cyber Security
Elastic has published an urgent security alert regarding a crucial weakness in Kibana, dubbed as CVE-2025-25012, which permits authenticated intruders to carry out random commands on impacted systems. The imperfection, scoring 9.9 on the CVSS v3.1 scale, arises from a...
Cyber Security
Essential tools for dynamic analysis of malware are crucial in identifying and comprehending present-day online dangers. These utilities operate suspicious applications in controlled environments to oversee their actions, which entail alterations in files, network...
Cyber Security
An advanced threat cluster identified as UAC-0212 has intensified efforts to breach vital infrastructure systems in Ukraine, as per a recent alert from CERT-UA (Government Computer Emergency Response Team of Ukraine). Since July 2024, these assaults have been...
Cyber Security
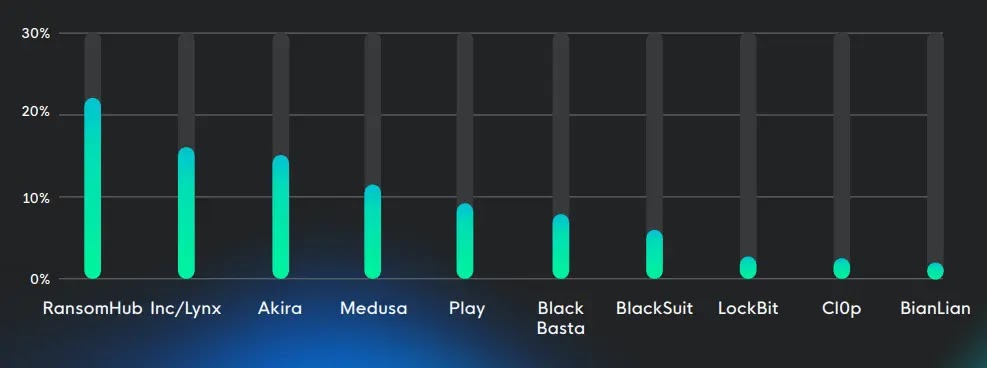
Recent studies uncover ransomware syndicates are hastening encryption timelines while embracing advanced evasion methods and data extortion tactics. According to a 2025 risk analysis by cybersecurity company Huntress, ransomware groups now require just 17 hours on...





