Cyber Security
Japan Airlines (JAL), the second largest carrier in the country, experienced a significant cyber strike on its systems early on Thursday morning, disrupting both local and international flight services. The assault initiated at 7:24 AM local time (2224 GMT) and aimed...

Cyber Security
As the year 2024 draws to a close, it’s time to shift our focus towards contemplating the landscape of public cybersecurity in the upcoming year 2025. An encouraging point to consider is that cybersecurity will persist as a paramount concern for the government,...
Cyber Security
A recently discovered security weakness, known as CVE-2024-43441, has been detected in Apache HugeGraph-Server, a widely used open-source graph database system. This particular flaw, identified as an Assumed-Immutable Data vulnerability leading to Authentication...

Cyber Security
The start of a new year always initiates a deluge of forecast articles; after a year’s passing, our news feed gets inundated with retrospective pieces. However, we often ponder whether experts made correct predictions in January on the unfolding events of the...
Cyber Security
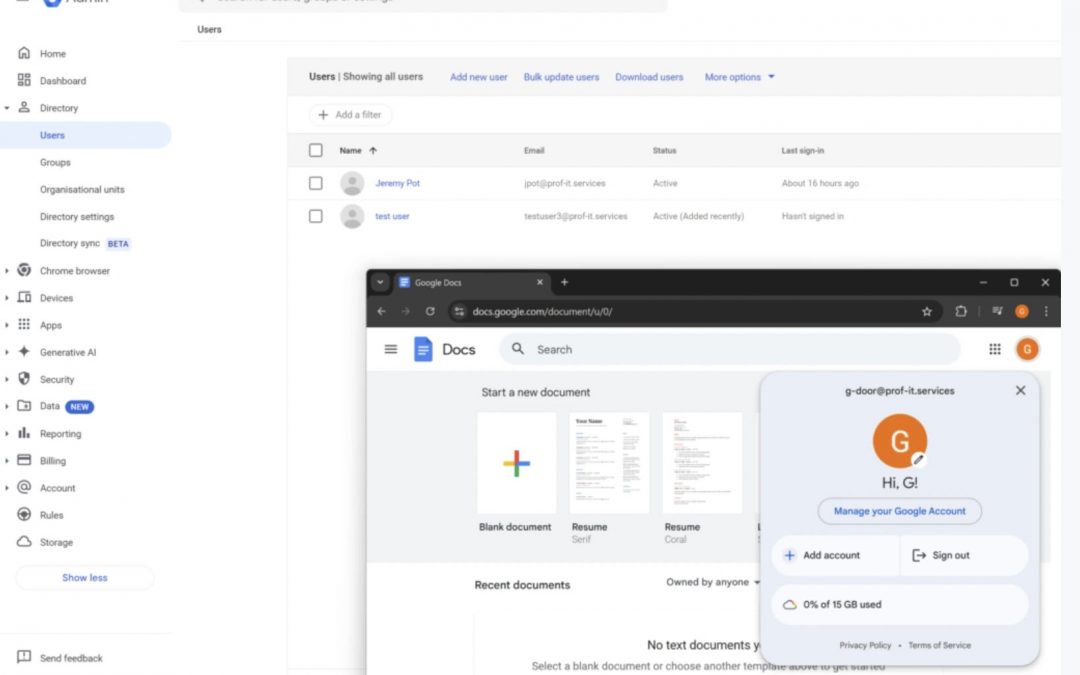
A recently discovered weakness, named “G-Door,” enables nefarious individuals to evade Microsoft 365 security protocols by leveraging unmanaged Google Docs accounts. This security vulnerability presents a significant risk to enterprises depending on Microsoft 365’s...



