Cyber Security
A Distributed Denial of Service (DDoS) assault is a malevolent effort to disrupt the regular operation of a targeted server, service, and network by inundating them with a surge of internet traffic from numerous compromised devices. Organizations face significant...

Cyber Security
The shortage of cybersecurity professionals is continuously expanding, leading to significant ramifications for companies globally. As per IBM’s 2024 Cost Of A Data Breach Report, over half of breached organizations are currently encountering severe deficits in...
Cyber Security
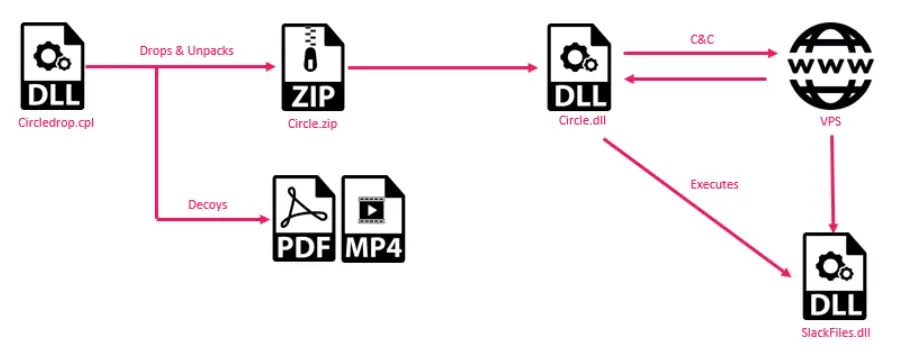
ElizaRAT is categorized as a form of malicious software that mainly targets Windows systems and operates as a RAT, allowing unauthorized access to be gained by threat actors on compromised machines. This malicious software is usually spread through phishing schemes or...
Cyber Security
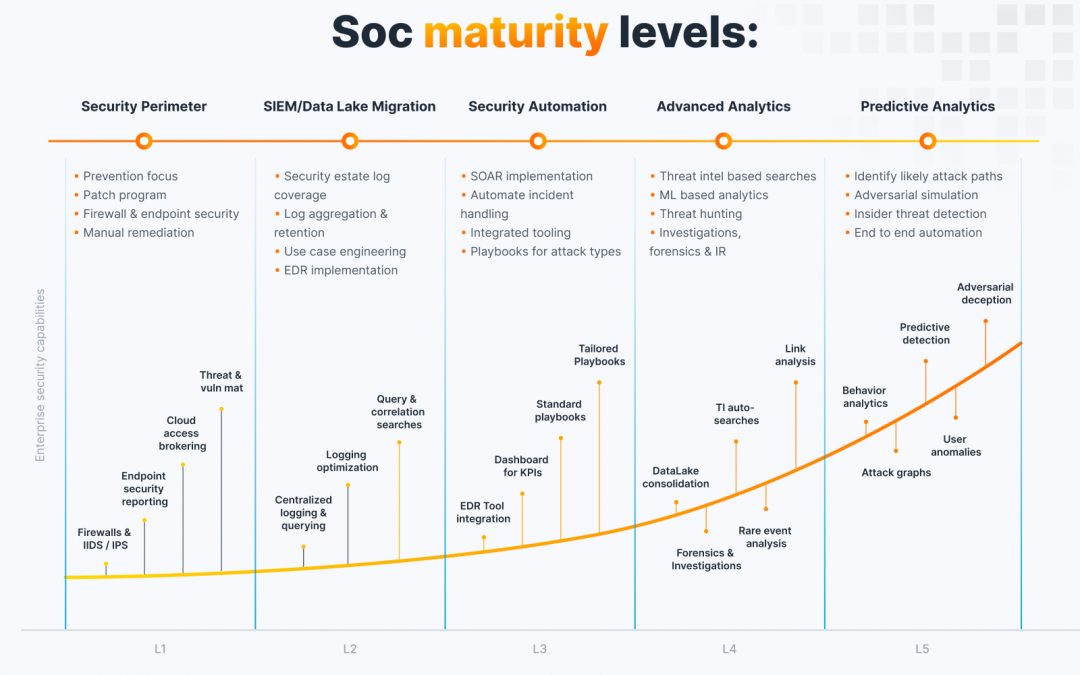
Exploring SOC pricing need not be daunting. I’ve been there—confronted with the question, “How much should we allocate for security?” You are not on your own. It involves a delicate equilibrium between safeguarding your enterprise and managing expenditures. SOC...
Cyber Security
Welcome to the latest edition of the Cybersecurity Bulletin, where you can discover the most recent developments and perspectives from the domain of cybersecurity. Keep informed and safeguarded with our featured stories. Stay abreast of the most recent risks and...



