
Cyber Security
“`html The realm of cybersecurity in 2025 is characterized by an escalation in sophisticated malware threats, with adversaries utilizing artificial intelligence, evasion strategies, and polymorphic code to circumvent conventional defenses. Stealers, ransomware,...
Cyber Security
“`html Security Operations Centers (SOCs) and Managed Security Service Providers (MSSPs) function at the cutting edge of cybersecurity, assigned with safeguarding entities from increasingly complex hazards. As adversaries hone their strategies, the necessity for...

Cyber Security
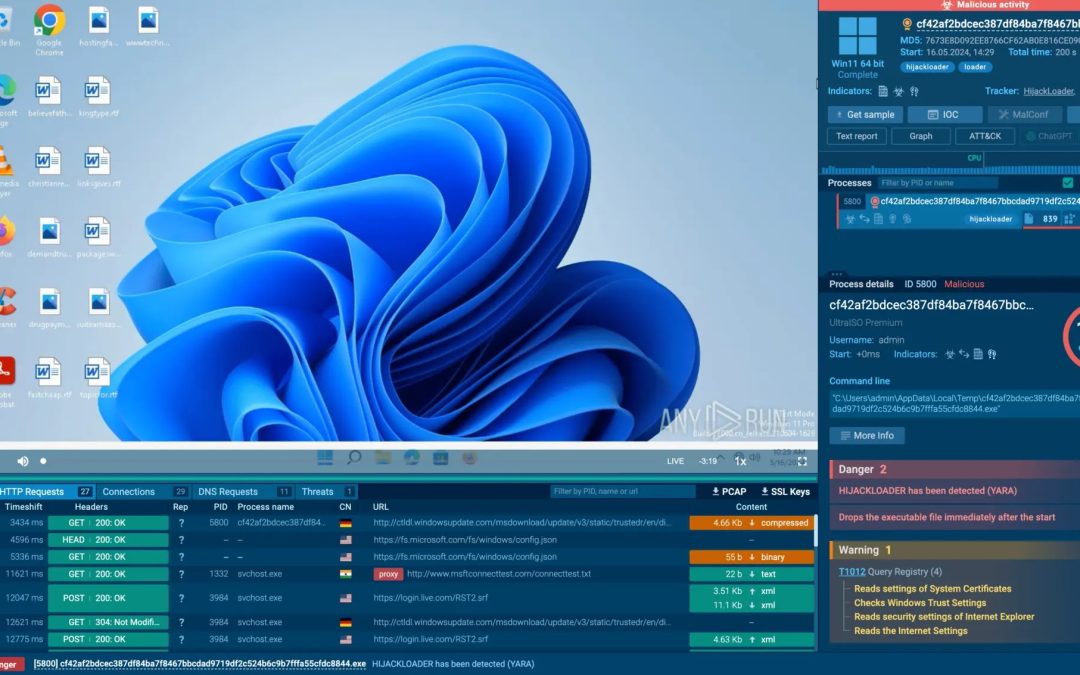
“`html As online threats evolve in complexity, the cybersecurity industry has sparked a funding rush, with new enterprises amassing $1.7 billion in April 2025 alone, just prior to the RSA Conference taking place in San Francisco. This influx highlights investor...
Cyber Security
“`html Microsoft has launched Windows 11 Insider Preview Build 26200.5600 (KB5058493) to the Dev Channel, bringing numerous new capabilities, enhancements, and resolutions for Windows Insiders. Declared by Amanda Langowski and Brandon LeBlanc, this update...

Cyber Security
“`html Microsoft has unveiled a novel “Prevent Screen Capture” functionality for Teams, which will obstruct unauthorized screenshots during meetings. Anticipated for global deployment in July 2025, this capability signifies Microsoft’s ongoing commitment to...

Cyber Security
“`html A recently discovered information-harvesting malware, termed PupkinStealer, crafted in C# utilizing the .NET framework; this compact yet potent malware focuses on sensitive user data, encompassing browser credentials, desktop files, messaging app...







