Cyber Security
An operation carried out jointly by INTERPOL and AFRIPOL has resulted in the apprehension of 1,006 individuals and the disassembly of 134,089 harmful infrastructures spanning 19 African nations. Termed as Operation Serengeti, the initiative specifically aimed at cyber...
Cyber Security
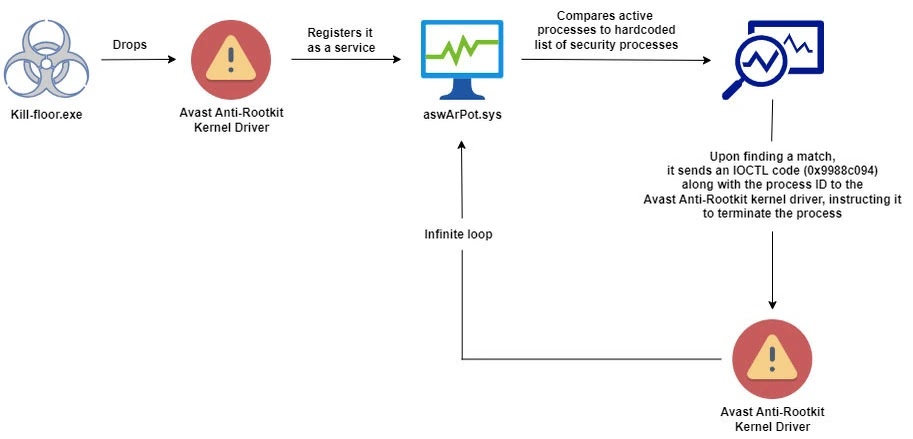
A harmful scheme has been unearthed wherein the malware utilizes a more sinister strategy, dropping the authentic Avast Anti-Rootkit driver (aswArPot.sys) to avoid detection. The malicious software leverages the driver’s deep access to halt security processes,...
Cyber Security
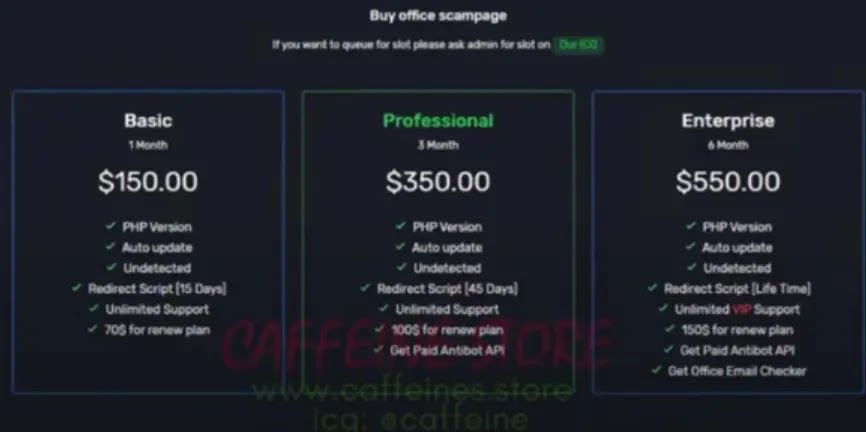
The Cybercrime Branch (CB) of Microsoft has shut down 240 deceitful websites that were exploited by the Egyptian phishing solution “ONNX.” Abanoub Nady, known online as “MRxC0DER,” launched and promoted “DIY” phish kits under the fake alias of “ONNX”. These kits were...
Cyber Security
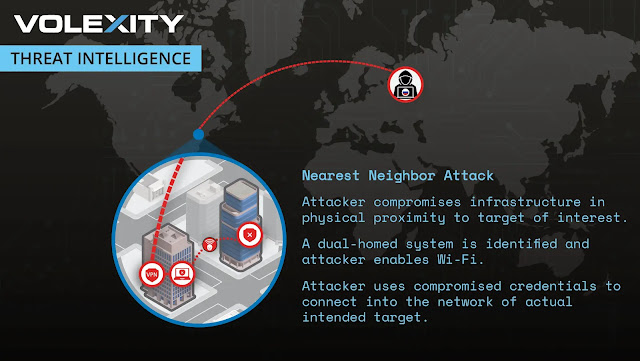
A hacking group sponsored by the Russian government, GruesomeLarch (also known as APT28 or Fancy Bear), has showcased an advanced new attack method named the “Nearest Neighbor Attack.” This technique enables remote hackers to infiltrate organizations by leveraging...
Cyber Security
In the year 2021, a series known as “A Journey in Organizational Resilience” was conducted. The subjects covered in this series continue to hold relevance today, and in many instances, they are even more crucial now, given the swift transformations witnessed in...
Cyber Security
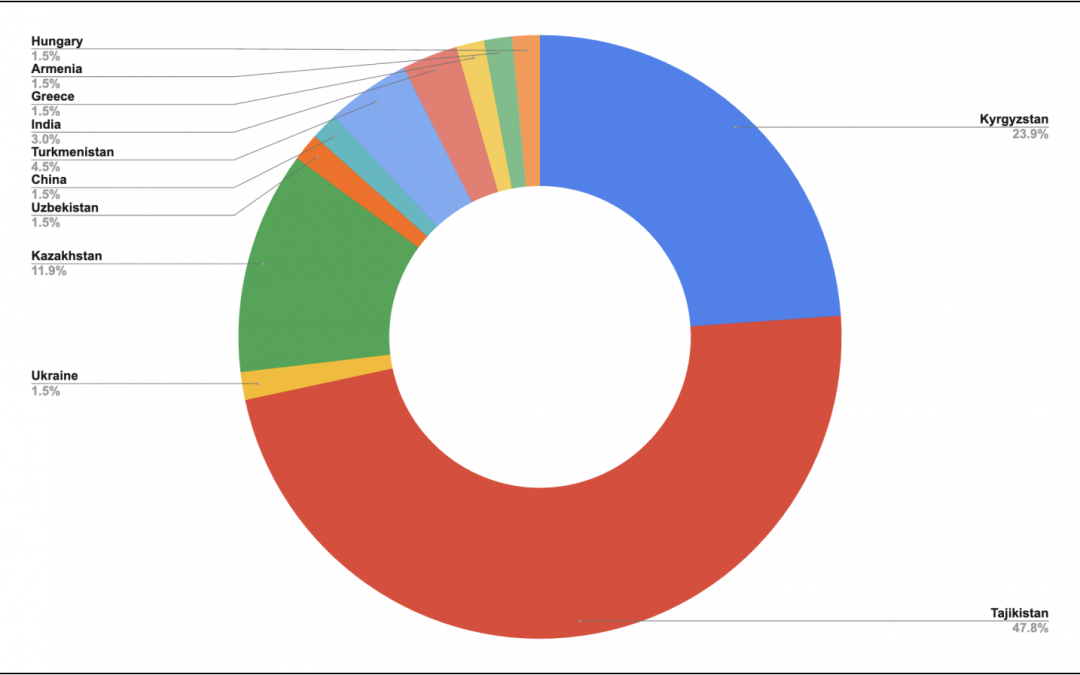
TAG-110, a menace group linked with Russia, is currently engaged in cyber-espionage operations targeting organizations in Central Asia, East Asia, and Europe. The primary focuses of this group include governmental bodies, NGOs, and academic establishments by deploying...




