Cyber Security
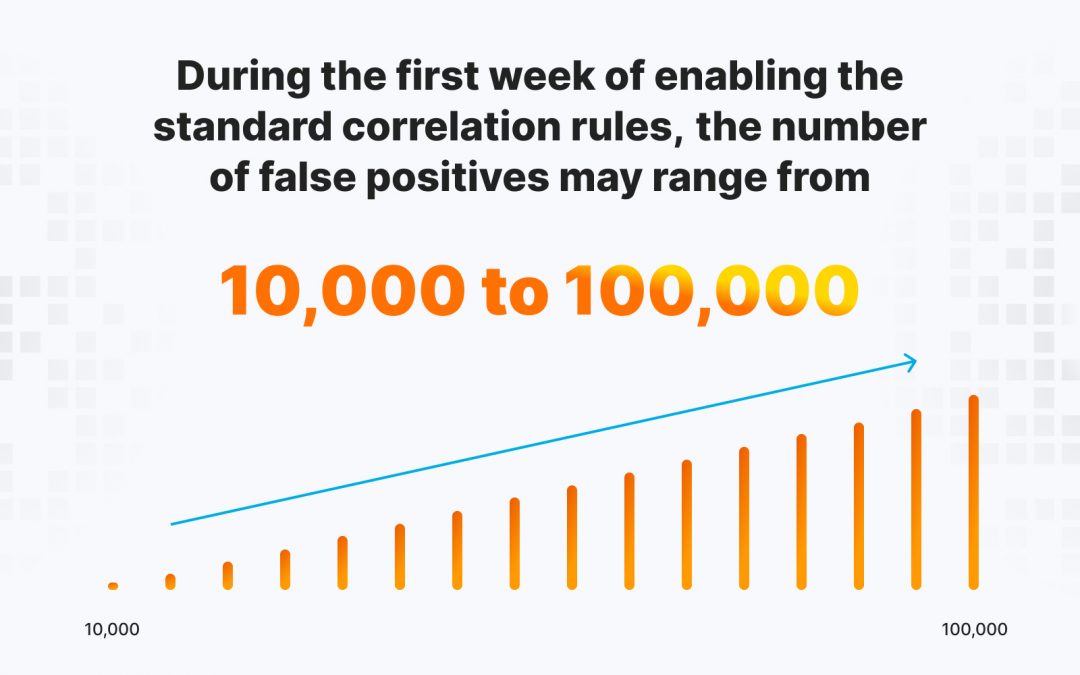
Supposing you’re overseeing an SIEM (Security Information and Event Management) setup, you understand the significance of centralized threat detection. SIEM gathers and scrutinizes data from various origins—such as your firewalls, applications, servers—and seeks...
Cyber Security
A sophisticated infiltration through the supply chain has been identified, exploiting entryways in well-known open-source package repositories, such as PyPI (Python), npm (JavaScript), Ruby Gems, and NuGet (.NET). This method of attack presents substantial risks for...
Cyber Security
Welcome to this edition of the Cybersecurity Newsletter, delivering the most recent updates and insights from the realm of cybersecurity. Keep yourself informed and shielded with our featured stories. Stay up-to-date on the newest risks and advancements in the...
Cyber Security
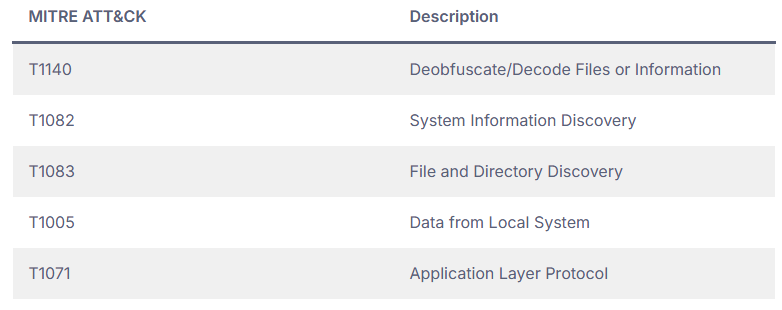
The realm of cyber dangers is complex and constantly evolving. Threat perpetrators are consistently enhancing their techniques, and fresh variants of data-stealing malware frequently emerge. Data theft tools are straightforward to use, cost-effective, and have minimal...

Cyber Security
At a time when companies are increasingly dependent on artificial intelligence (AI) and advanced data capabilities, the importance of IT services is more crucial than ever. Nonetheless, despite the progress in technology, business leaders are growing more dissatisfied...
Cyber Security
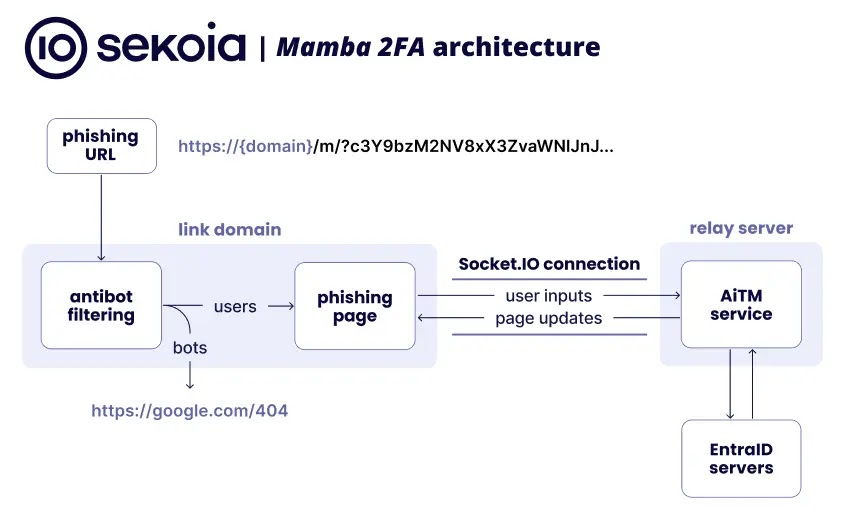
Deceptive cyber schemes known as phishing attacks involve threat actors masquerading as trusted sources to deceive individuals into disclosing sensitive data such as “passwords” or “financial information.” These fraudulent activities are...





