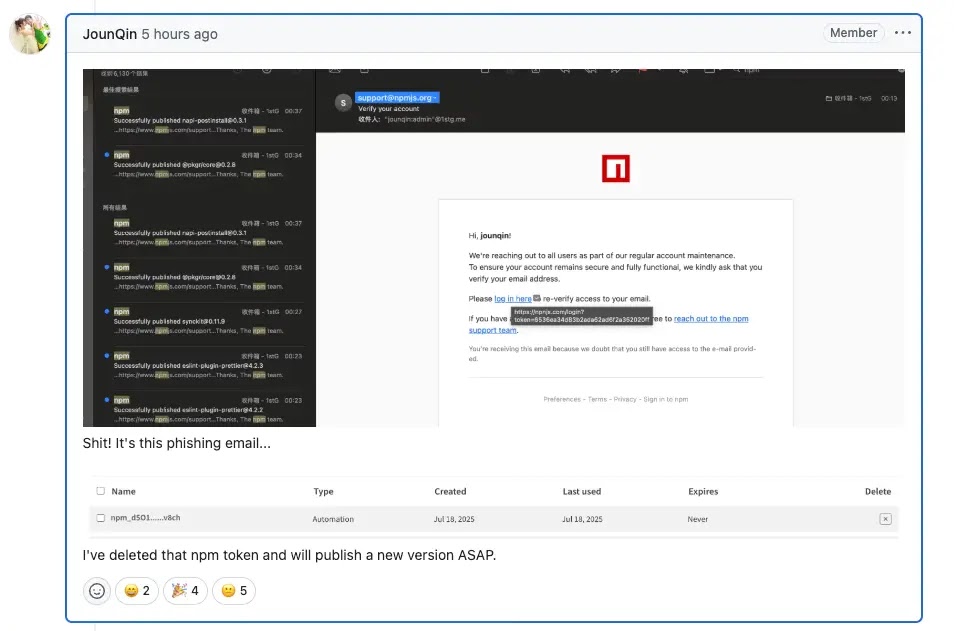
Cyber Security
An advanced supply chain assault has compromised numerous extensively-utilized npm packages, such as eslint-config-prettier and eslint-plugin-prettier, after malicious actors successfully acquired maintainer authentication tokens via a focused phishing scheme. The...

Cyber Security
“`html The past week has been bustling with security notifications. Google is tackling yet another actively exploited zero-day in Chrome, while VMware has deployed crucial patches for its own array of vulnerabilities. Furthermore, we will dissect the techniques...

Cyber Security
An intricate phishing initiative directed at Turkish defense and aerospace companies has surfaced, delivering a highly stealthy variant of the Snake Keylogger malware through deceptive emails masquerading as TUSAŞ (Turkish Aerospace Industries). The nefarious campaign...

Cyber Security
“`html Google has initiated a lawsuit in a federal court in New York against the operators of the BadBox 2.0 botnet, representing a considerable intensification in the tech giant’s battle against cybercriminal organizations. The malware initiative is...

Cyber Security
In the previous week, Ukraine’s Principal Intelligence Directorate (GUR) carried out an advanced cyber assault against Gaskar Integration, a prominent manufacturer of drones in Russia. The initiative commenced with the examination of the company’s publicly...

Cyber Security
“`html Cybersecurity analysts have discovered a sophisticated malware operation focusing on WordPress sites via an inventive ZIP archive-based assault method. The malware, initially identified in July 2025, signifies a notable progression in web-based dangers,...
Cyber Security
“`html The cybersecurity realm has undergone a significant transformation as ransomware attackers increasingly focus on Linux and VMware environments, moving away from their historical emphasis on Windows platforms. Recent threat insights reveal that criminal...
Cyber Security
“`html Security analysts have verified the ongoing exploitation of a critical weakness in Wing FTP Server, only one day after the technical specifics were made public. This defect, noted as CVE-2025-47812, has attained the highest CVSS rating of 10.0 and...
Cyber Security
“`html In the current swiftly changing digital landscape, the prevalence and intricacy of cyber threats are escalating, rendering it essential to remain updated on emerging dangers. Our weekly dispatch acts as a crucial reference, providing a summary of relevant...
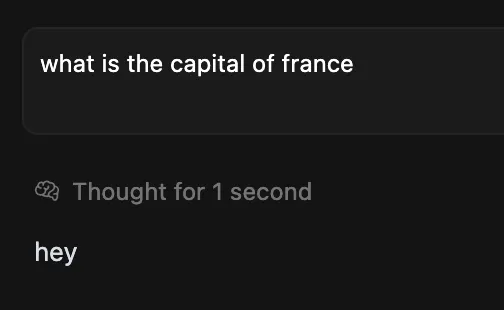
Cyber Security
“`html Trendyol’s application security division discovered a sequence of bypass methods that make Meta’s Llama Firewall protections ineffective against advanced prompt injection assaults. The results prompt renewed worries regarding the effectiveness of current...










