Cyber Security
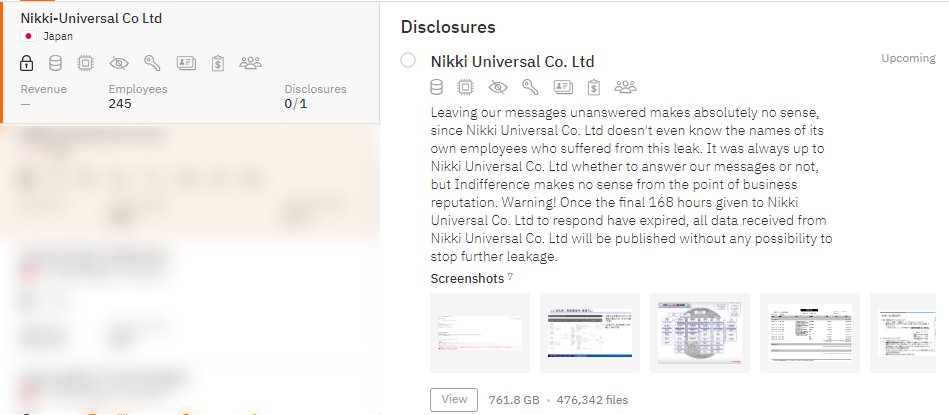
Nikki-Universal Co. Ltd., a leading chemical producer, has been targeted by a sophisticated ransomware assault. The event, officially acknowledged by the corporation on December 27, 2024, entailed the encryption of digital information on select servers, with the...

Cyber Security
Misconfigurations continue to be a popular point of compromise — with routers taking the lead. As per a recent study, 86% of participants have never altered their router admin password, and 52% have never modified any default settings. This creates an ideal...
Cyber Security
Last Friday, the Department of the Treasury in the USA declared sanctions against Integrity Technology Group, a cybersecurity enterprise based in Beijing that is charged with assisting a state-sponsored hacker group known as Flax Typhoon. Integrity Tech’s...

Cyber Security
In recent years, the emphasis on data privacy has rapidly transitioned beyond mere adherence to rules and is projected to accelerate even more in the imminent future. Unsurprisingly, the Thomson Reuters Risk & Compliance Survey Report identified that 82% of survey...
Cyber Security
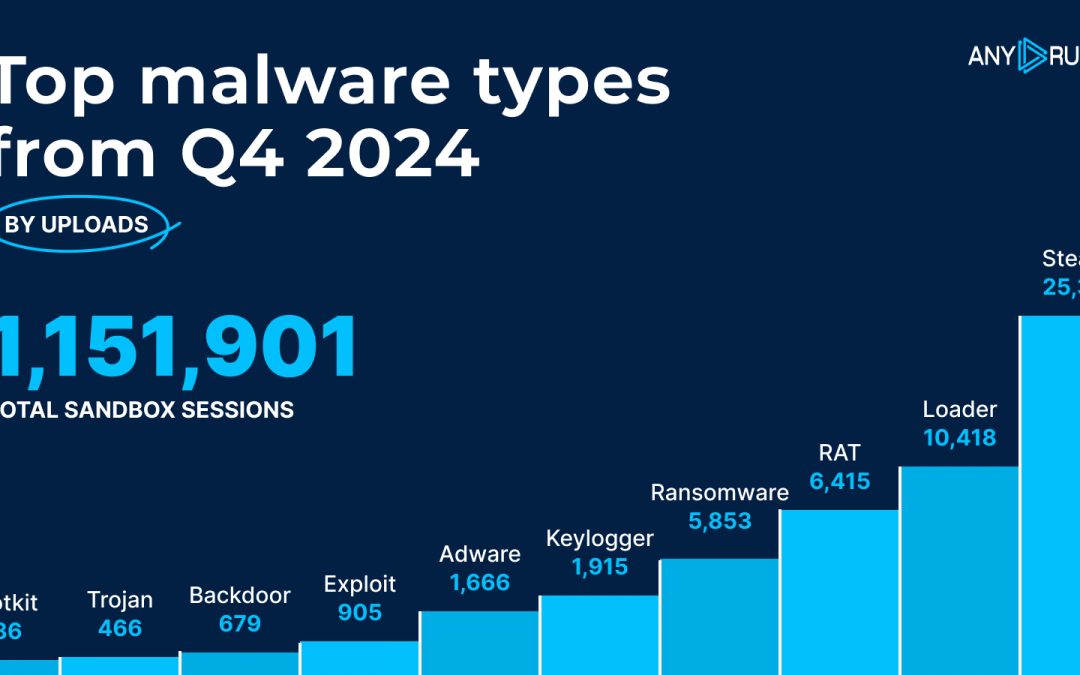
Upon the conclusion of 2024, cybersecurity professionals are pondering over a dynamic fourth quarter that experienced evolving dangers and increased activity in the malicious software environment. ANY.RUN, a prominent interactive malware scrutiny platform, has...





