Cyber Security
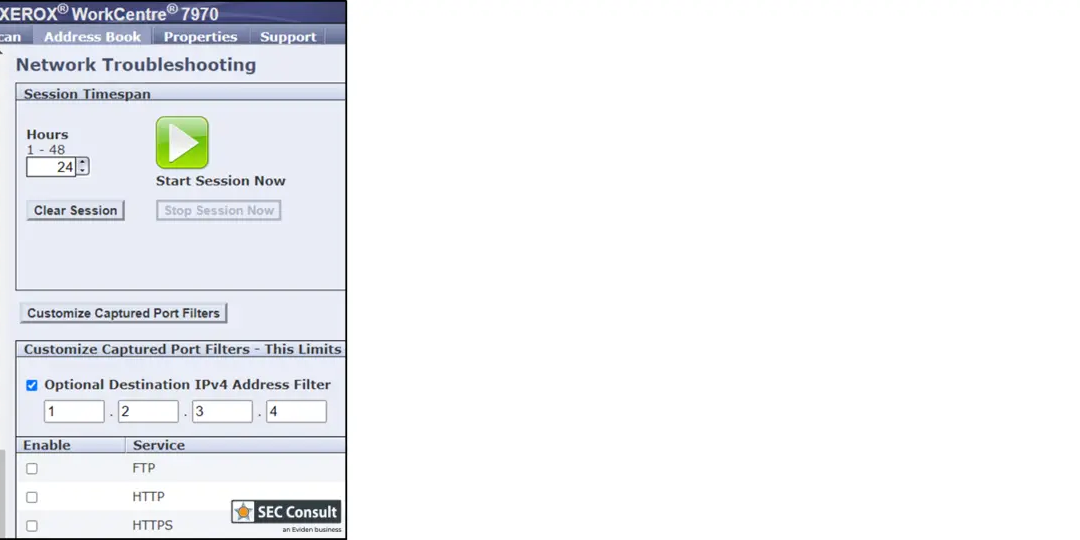
There has been a critical security flaw identified in various Xerox printer models, enabling individuals with administrative privileges to gain full control over the devices. SEC Consult has reported a significant vulnerability, recognized as CVE-2024-6333, impacting...

Cyber Security
Every business operation hinges on the protection of data. In today’s landscape, the security of crucial data and communication relies on traditional methods of cryptography, like the RSA algorithm. While these algorithms offer protection against current...
Cyber Security
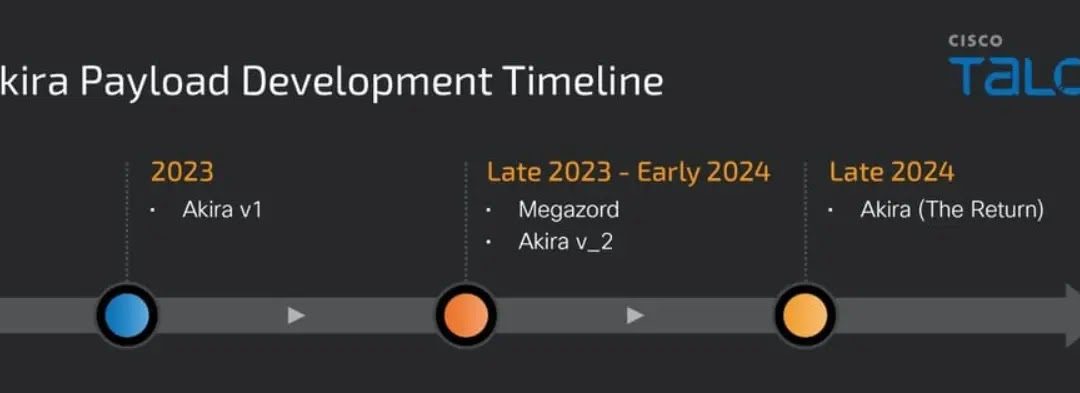
The actors behind Akira Ransomware are working on a Rust Variant to target ESXi servers. Initially detected in March 2023, this ransomware is designed to infiltrate both Windows and Linux systems. Utilizing a double-extortion strategy, this ransomware strain has...
Cyber Security
Through a notable action that is poised to transform the cybersecurity field, Sophos has publicized its acquisition of SecureWorks for $859 million. The complete cash transaction, unveiled on the 21st of October, 2024, unites two distinguished players in the...
Cyber Security
Welcome to the current week’s Cybersecurity Bulletin, presenting you with the freshest updates and insights from the realm of cybersecurity. Stay knowledgeable and shielded with our prime narratives. Stay up to date on the most recent risks and advancements in the...
Cyber Security
Cisco has initiated an inquiry into a potential cybersecurity issue and has proactively deactivated its public DevHub portal. Confirmation came on the 18th of October, 2024, that the organization is investigating allegations of an unauthorized party supposedly...




